Security
Concepts
1. Security Primitives
2. Authentication
3. TLS
4. Certificates API
5. KubeConfig
6. API Groups
7. Authorization
8. RBAC
9. CLuster Roles
10. Image Security - Security Contexts
11. Network Policies
Securityprimitives
kubernetes related security
secure the "kube-apiserver" in two ways
1. who can access the kube-apiserver --> "Authentication" like username and passwords, username and Tokens,
Certificates, External Authentication providers(LDAP) and for machines its Service Accounts
2. What can they do in kube-apiserver --> "Authorization" using RBAC Authorization, Node Authorization, Webhook mode,
ABAC Authorization(Attribute Based Access Controls)
All communication between k8s components achieved with TLS encryption.
How about between application --> by default all pods can access all other pods with in the cluster,
we can use "network policies" to restrict the access between pods.
k8sAuthentication
k8s can be accessbed by
1. Admins --> ClusterAdmin
2. Developers --> Application Developers who gonna host an application in k8s
3. Endusers --> applications hosted in pods can be accessed
4. Bots(Service Accounts, Other services, third party services)
Users are managed by "kube-apiserver"
------------------------------------------->
1. Static Password File
2. Static Token File
3. Certificates
4. Identity services(LDAP, kerberos)
1. Static Password File
user-details.csv
--------------------------->
password123,user1,u001
password12,user2,u002
kube-apiserver.service:
------------------------>
--basic-auth-file=user-details.csv
curl -vk https://master-node-ip:6443/api/v1/pods -u "user1:password123"
2. Static Token File
user-token-details.csv:
-------------------------->
sdjhflsdfiriwlerwqerowpjf84043w,user10,u001
wewerweirwreowwoewqerowpjf8werw,user11,u002
kube-apiserver.service:
---------------------------------------------->
--token-auth-file=user-token-details.csv
curl -vk https://master-node-ip:6443/api/v1/pods --header "Authorization: Bearer sdjhflsdfiriwlerwqerowpjf84043w"
Create a file with user details locally at /tmp/users/user-details.csv
# User File Contents
password123,user1,u0001
password123,user2,u0002
password123,user3,u0003
password123,user4,u0004
password123,user5,u0005
/etc/kubernetes/manifests/kube-apiserver.yaml
----------------------------------------------------------------------------->
apiVersion: v1
kind: Pod
metadata:
name: kube-apiserver
namespace: kube-system
spec:
containers:
- command:
- kube-apiserver
<content-hidden>
image: k8s.gcr.io/kube-apiserver-amd64:v1.11.3
name: kube-apiserver
volumeMounts:
- mountPath: /tmp/users
name: usr-details
readOnly: true
volumes:
- hostPath:
path: /tmp/users
type: DirectoryOrCreate
name: usr-details
Modify the kube-apiserver startup options to include the basic-auth file
----------------------------------------------------------------------------------------->
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
name: kube-apiserver
namespace: kube-system
spec:
containers:
- command:
- kube-apiserver
- --authorization-mode=Node,RBAC
<content-hidden>
- --basic-auth-file=/tmp/users/user-details.csv
Create the necessary roles and role bindings for these users:
------------------------------------------------------------------->
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["pods"]
verbs: ["get", "watch", "list"]
---
# This role binding allows "jane" to read pods in the "default" namespace.
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: User
name: user1 # Name is case sensitive
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role #this must be Role or ClusterRole
name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to
apiGroup: rbac.authorization.k8s.io
after running above we can access kube-apiserver as --> curl -v -k https://localhost:6443/api/v1/pods -u "user1:password123"
Certificates:
----------------------------------------------------->
1. TLS Basics
2. TLS in kubernetes - Certificate creation
demossltls
Sender --------> Reciever
"symmetric encryption": Same key is used to encrypt and decrypt both at sender-end and reciever-end
"asymmetric encryption": This encryption uses pair of keys, a private key and a public key
ssh-key example:
--------------------->
in the users system:
----------------------------------------------->
ssh-keygen generates both private and public keys
id_rsa
id_rsa.pub
in the servers ~/.ssh/Authorizedkeys:
-------------------------------------------------------------------------------------------------------------------------->
copy users public key(id_rsa.pub) to servers Authorizedkeys file to securely access the server(using asymmetric encryption)
Web servers example:
---------------------------------------------------------->
as we did it in ssh-keygen(which creates private and public keys) we can do same for webserver TLS encryption also
to generate private and public key pair can use "openssl"
"private key(my-bank.key) creation":
--------------------------------------->
openssl genrsa -out my-bank.key 1024
"public key(mybank.pem) creation":
-------------------------------------------------->
openssl rsa -in my-bank.key -pubout > mybank.pem
MacBook-Pro:6.Security bharathdasaraju$ mkdir generate_tls_public-private_keys
MacBook-Pro:6.Security bharathdasaraju$ cd generate_tls_public-private_keys
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$ openssl genrsa -out my-bank.key 1024
Generating RSA private key, 1024 bit long modulus
.++++++
................................................................++++++
e is 65537 (0x10001)
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$ ls -rtlh
total 8
-rw-r--r-- 1 bharathdasaraju staff 887B 22 Sep 16:47 my-bank.key
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$ openssl rsa -in my-bank.key -pubout > mybank.pem
writing RSA key
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$ ls -rlth
total 16
-rw-r--r-- 1 bharathdasaraju staff 887B 22 Sep 16:47 my-bank.key
-rw-r--r-- 1 bharathdasaraju staff 272B 22 Sep 16:48 mybank.pem
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$
How to sign certificates with certificate authority:
---------------------------------------------------------->
popular CAs are symantec, global sign, digicert etc..
Certificate Signing Request(CSR)
-------------------------------------------------------------->
We need to generate a Certificate Signing Request(CSR) by using the private key(my-bank.key) we generated earlier
openssl req -new -key my-bank.key -out my-bank.csr -subj "/C=SG/ST=SG/O=my-bank, Inc./CN=my-bank.com"
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$ openssl req -new -key my-bank.key -out my-bank.csr -subj "/C=SG/ST=SG/O=my-bank, Inc./CN=my-bank.com"
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$ ls -rtlh
total 24
-rw-r--r-- 1 bharathdasaraju staff 887B 22 Sep 16:47 my-bank.key
-rw-r--r-- 1 bharathdasaraju staff 272B 22 Sep 16:48 mybank.pem
-rw-r--r-- 1 bharathdasaraju staff 607B 22 Sep 17:11 my-bank.csr
MacBook-Pro:generate_tls_public-private_keys bharathdasaraju$
the certificate authorities check our csr file and sign and send the certificates to us.
how to make sure that the certificate is signed by legitimate CA....
like CA is a valid CA and that the certificate is infact signed by Symantec and not by some fake CA names semantech.
The CAs themselves have set of public and private keypairs.
The CA is use their private keys to sign the certificates, the public keys of all the CAs are built in to the browsers as shown in the image CAs_pulbic_certs_in_browser.png
The public keys of all the CAs are built in to the browsers.
The browser uses the public key of the CA to validate that the certificate is actually signed by the CA themselves.
Now these are the public CAs that help us ensure the public websites we visit, like our banks, email etc are legitimate.
However they dont help you to validate sites hosted privately say within your organization.
For example, for accessing your payroll or internal email applications.For that you can host your own private CAs.
Most of the companies like Symantec,Comodo,GlobalSign,digicert have a private offering of their services.
A CA server that you can deploy internally with in your company.
You can then have the public key of your internal CA server installed on all your employees browsers and establish secure connectivity
within your organization.
usually public keys ends with "*.crt" (or) "*.pem"
server.crt
server.pem
client.crt
client.pem
usually private keys ends with "*.key" (or) "*-key.pem"
server.key
server-key.pem
client.key
client-key.pem
TLSink8s
"Server Certificates": Serving certificates
-------------------------------------------------->
"private_key": my-bank.key(my-bank-key.pem)
"public_key": mybank.pem(mybank.crt)
"Certificate Authority": Root certificates
----------------------------------------------->
CA has its own set of private and public_keys
CA public keys already available in all browsers to validate its signed by correct CA
"Client Certificates":
-------------------------------------------------->
client.key(client-key.pem) --> "private key"
client.pem(client.crt) --> "public key"
In kubernetes communication between all the k8s components needs to be secured.
i.e. kube-apiserver to kube-scheduler....kubelet to kube-apiserver ...kube-apiserver to kube-controllermanager etc...
Server certificate for Server components in k8s :
--------------------------------------------------->
1."kube-apiserver" --> apiserver.crt and apiserver.key
2."etcd server" --> etcdserver.crt and etcdserver.key
3."kubelet server" --> kubelet.crt and kubelet.key
Client certificates for Client components in k8s:
--------------------------------------------------------->
4."admins(we)" --> we need admin.crt and admin.key to authenticate with the "kube-apiserver"
5."kube-scheduler" --> scheduler.crt and scheduler.key
6."kube-controller-manager" --> controller-manager.crt and controller-manager.key
7."kube-proxy" --> kube-proxy.crt and kube-proxy.key
The server components also talks to themseves as well...lets say "kube-apiserver" talks to "etcd-server" ..
so at that time kube-apiserver is client for the etcd-server...kube-apiserver can use same server certificates (or) we can generate another certs for this purpose only.
8."apisever-etcd client" --> apiserver-etcd-client.crt and apiserver-etcd-client.key
and also kube-apiserver talks to the kubelet server, so at that time kube-apiserver is client for kubelet
kube-apiserver can use same server certificates (or) we can generate another certs for this purpose only.
9."apiserver-kubelet client" --> apiserver-kubelet-client.crt and apiserver-kubelet-client.key
Of course we need Certificate Authority(CA) to sign abd validate above all 9 certificates.
CA has its own certs i.e. 10. "CA certs" --> ca.crt and ca.key
opensslapiserverconf
[req]
req_extensions = v3_req
distinguished_name = req_distinguished_name
[req_distinguished_name]
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = kubernetes
DNS.2 = kubernetes.default
DNS.3 = kubernetes.default.svc
DNS.4 = kubernetes.default.svc.cluster.local
DNS.5 = k8s-master.local
IP.1 = 10.254.0.1
IP.2 = 192.168.1.230
kubeletconfig
kind: KubeletConfiguration
apiVersion: kubelet.config.k8s.io/v1beta1
authentication:
x509:
clientCAFile: "/var/lib/kubernetes/ca.pem"
authorization:
mode: webhook
clusterDomain: "cluster.local"
clusterDNS:
- "10.32.0.10"
podCIDR: "${POD_CIDR}"
resolvConf: "/run/systemd/resolve/resolv.conf"
runtimeRequestTimeout: "15m"
tlsCertFile: "/var/lib/kubelet/node01.crt"
tlsPrivateKeyFile: "/var/lib/kubelet/node01.key"
k8sapiconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority: ca.crt
server: https://kube-apiserver:6443
name: kubernetes
kind: config
users:
- name: kubernetes-admin
user:
client-certificate: admin.crt
client-key: admin.key
generatetlsink8s
Server certificate for Server components in k8s :
--------------------------------------------------->
1."kube-apiserver" --> apiserver.crt and apiserver.key
2."etcd server" --> etcdserver.crt and etcdserver.key
3."kubelet server" --> kubelet.crt and kubelet.key
Client certificates for Client components in k8s:
--------------------------------------------------------->
4."admins(we)" --> we need admin.crt and admin.key to authenticate with the "kube-apiserver"
5."kube-scheduler" --> scheduler.crt and scheduler.key
6."kube-controller-manager" --> controller-manager.crt and controller-manager.key
7."kube-proxy" --> kube-proxy.crt and kube-proxy.key
8."apisever-etcd client" --> apiserver-etcd-client.crt and apiserver-etcd-client.key
9."apiserver-kubelet client" --> apiserver-kubelet-client.crt and apiserver-kubelet-client.key
CA Certs:
---------------------------------------------------------->
10. "CA certs" --> ca.crt and ca.key
to generate certs we can use "openssl" tool(Someother tools easyrsa and cfssl also available)
"tls certs generation for CA":
------------------------------------------------------------------------------------------------------------------------------->
1. "generate private key for CA i.e. ca.key":
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl genrsa -out ca.key 2048
Generating RSA private key, 2048 bit long modulus
...................................................................+++
........+++
e is 65537 (0x10001)
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
2. "Generate csr(certificate signing request) using ca.key":
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl req -new -key ca.key -subj "/CN=KUBERNETES-CA" -out ca.csr
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
ca.csr ca.key
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
3. "Sign the csr and create crt using with self-signed private key(ca.key)":
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl x509 -req -in ca.csr -signkey ca.key -out ca.crt
Signature ok
subject=/CN=KUBERNETES-CA
Getting Private key
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
going forrward we will use the CA key pairs to sign them.
the CA now has its own "private key(ca.key)" and the "root certificate(ca.crt)" file.
"Generate client tls certificates":
------------------------------------------------------------------------------------------------------------------------------->
"admins(we)" --> we need admin.crt and admin.key to authenticate with the "kube-apiserver"
1. "generate private key for admin i.e. admin.key":
----------------------------------------------------------------------->
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl genrsa -out admin.key 2048
Generating RSA private key, 2048 bit long modulus
....................+++
............................................+++
e is 65537 (0x10001)
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
admin.key ca.crt ca.csr ca.key
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
2. "Generate csr(certificate signing request) using admin.key":
----------------------------------------------------------------------->
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl req -new -key admin.key -subj "/CN=kube-admin" -out admin.csr
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
admin.csr admin.key ca.crt ca.csr ca.key
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
While creating csr we can specify groups(O=system:masters) for k8s admin privileges
like i.e. openssl req -new -key admin.key -subj "/CN=kube-admin/O=system:masters" -out admin.csr
3. "Sign the csr and create crt using with the CA private key and public key(CA keypairs generated in last step)":
-------------------------------------------------------------------------------------------------------------------->
This make this as valid certificate with in the entire cluster.
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl x509 -req -in admin.csr -CA ca.crt -CAkey ca.key -out admin.crt
Signature ok
subject=/CN=kube-admin
Getting CA Private Key
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
admin.crt admin.csr admin.key ca.crt ca.csr ca.key ca.srl
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
What we can do with admin.key and admin.crt is we can authenticate kube-apiserver using this private and public keys like below
"curl https://kube-apiserver:6443/api/v1/pods --key admin.key --cert admin.crt --cacert ca.crt"
Kube-apiserver is kubernetes
-------------------------------------------------------->
kubernetes
kubernetes.default
kubernetes.default.svc
kubernetes.default.svc.cluster.local
1. "generate private key":
------------------------------------------------------------->
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl genrsa -out apiserver.key 2048
Generating RSA private key, 2048 bit long modulus
..................................................................................................................................+++
.....+++
e is 65537 (0x10001)
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
admin.crt admin.csr admin.key apiserver.key ca.crt ca.csr ca.key ca.srl
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
2. "generate csr with lot of alternative names" using a file called openssl-apiserver.conf
---------------------------------------------------------------------------------------->
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl req -new -key apiserver.key -subj "/CN=kube-apiserver" -out apiserver.csr -config openssl-apiserver.conf
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
admin.crt admin.key apiserver.key ca.csr ca.srl
admin.csr apiserver.csr ca.crt ca.key openssl-apiserver.conf
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
3. "Sign the csr and create crt using with the CA private key and public key(CA keypairs generated in last step)":
--------------------------------------------------------------------------------------------------------------------------->
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl x509 -req -in apiserver.csr -CA ca.crt -CAkey ca.key -out apiserver.crt
Signature ok
subject=/CN=kube-apiserver
Getting CA Private Key
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
admin.crt admin.key apiserver.csr ca.crt ca.key openssl-apiserver.conf
admin.csr apiserver.crt apiserver.key ca.csr ca.srl
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
certsinetcd
#Found in the path /etc/kubernetes/manifests
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
component: etcd
tier: control-plane
name: etcd
namespace: kube-system
spec:
containers:
- command:
- etcd
- --advertise-client-urls=https://172.17.0.17:2379
- --cert-file=/path-to-certs/etcdserver.crt
- --key-file=/path-to-certs/etcdserver.key
- --client-cert-auth=true
- --data-dir=/var/lib/etcd
- --initial-advertise-peer-urls=https://172.17.0.17:2380
- --initial-cluster=master=https://172.17.0.17:2380
- --listen-client-urls=https://127.0.0.1:2379,https://172.17.0.17:2379
- --listen-metrics-urls=http://127.0.0.1:2381
- --listen-peer-urls=https://172.17.0.17:2380
- --name=master
- --peer-cert-file=/path-to-certs/etcdpeer1.crt
- --peer-client-cert-auth=true
- --peer-key-file=/path-to-certs/etcdpeer1.key
- --peer-trusted-ca-file=/etc/kubernetes/pki/etcd/ca.crt
- --snapshot-count=10000
- --trusted-ca-file=/etc/kubernetes/pki/etcd/ca.crt
image: k8s.gcr.io/etcd:3.3.15-0
viewk8scerts
#k8s
"kube-apiserver": cat /etc/kubernetes/manifests/kube-apiserver.yaml
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl x509 -in apiserver.crt -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 13415778325770680942 (0xba2e6b4eb4f23a6e)
Signature Algorithm: sha1WithRSAEncryption
Issuer: CN=KUBERNETES-CA
Validity
Not Before: Sep 22 22:42:58 2021 GMT
Not After : Oct 22 22:42:58 2021 GMT
Subject: CN=kube-apiserver
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:bc:89:64:af:08:09:a0:04:c6:a5:c5:29:d7:10:
df:e1:2d:28:a5:1b:3e:77:2a:76:09:17:8e:95:fe:
9e:7d:f9:b5:7b:01:7d:88:2e:28:ab:36:f2:f9:b6:
dd:84:fb:2f:f4:ce:bc:81:be:6b:df:60:cd:f5:a6:
d1:5d:be:09:83:7e:19:ef:52:d2:56:0f:24:bc:8d:
74:72:48:fa:e2:fd:63:2f:30:80:3a:3c:d9:41:d7:
62:af:84:bb:e6:bb:2e:0b:96:dc:a6:c6:1f:81:ef:
c1:31:e7:85:9a:1d:74:0c:c6:3a:c7:04:b2:a1:65:
44:e8:1b:8a:b7:c8:f9:d2:7e:e5:3a:45:ef:5e:52:
c3:a7:1e:94:4e:4f:c9:0d:77:51:72:31:79:07:65:
4c:23:b0:b5:e2:92:eb:1b:8e:ce:14:f4:dd:32:1a:
1b:e1:44:ca:e8:e1:4c:84:bb:00:bf:30:d2:42:e3:
4f:bd:11:86:96:f2:ce:e7:45:0c:36:aa:09:2f:8a:
f3:02:ed:27:1f:25:88:cd:20:64:6e:f5:e6:29:15:
84:c9:aa:c8:1e:4a:0e:d5:03:6f:1b:59:a0:b4:d1:
b8:77:20:f2:0c:41:fe:a9:69:80:79:81:d2:df:b4:
ae:c0:21:e5:cc:e9:be:ea:90:d2:44:1e:c8:38:85:
5f:d1
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
65:8a:0f:cb:41:b7:43:b8:c3:72:1c:cf:2c:a6:c4:64:91:31:
e5:b2:c0:95:b0:57:14:56:34:a9:fe:d4:41:50:9c:f9:4a:43:
64:e6:4f:e9:2a:dc:41:9f:79:1b:93:b8:7b:86:16:b1:6f:3f:
16:4a:c3:f6:f8:ef:33:97:a1:a6:ef:e0:4f:89:45:25:72:be:
2b:a9:67:a1:97:09:b4:8b:40:e2:b0:b8:41:66:53:ec:9d:a7:
60:51:66:bd:3d:db:1c:af:7b:fb:71:5d:39:7e:c7:aa:93:07:
b2:f2:de:f0:6e:67:06:dd:e1:3f:39:4c:f8:2d:26:fd:38:78:
2f:fe:53:f6:cc:01:17:d6:a2:f2:6e:93:48:8d:b1:07:45:51:
ca:c7:b9:bf:87:8f:0d:70:cd:5b:64:92:8c:9e:92:d9:56:d7:
90:2b:fa:9e:b6:03:28:22:f3:6b:9c:71:5a:3d:cb:79:b1:ee:
d3:8b:57:26:60:1f:85:c4:dd:9d:83:04:6c:75:06:60:92:e1:
1c:5f:1e:02:82:d1:bf:c7:11:bd:e7:5e:14:18:32:79:74:d1:
ba:b7:c1:cf:fc:e8:20:ea:fa:77:43:13:79:d9:6d:a9:75:dd:
f2:4a:24:52:c0:dc:a7:9a:98:01:4d:0a:e6:d1:15:0c:bb:96:
69:61:07:b9
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl x509 -in admin.crt -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 13415778325770680941 (0xba2e6b4eb4f23a6d)
Signature Algorithm: sha1WithRSAEncryption
Issuer: CN=KUBERNETES-CA
Validity
Not Before: Sep 22 22:21:45 2021 GMT
Not After : Oct 22 22:21:45 2021 GMT
Subject: CN=kube-admin
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d3:3e:1f:b3:49:45:a2:9d:b9:f8:8a:3d:79:a8:
bb:de:9a:6a:d7:e7:64:e5:3d:2e:1f:3e:0a:a1:21:
77:44:a8:6e:37:2a:bd:4e:19:bf:7b:42:d6:49:a1:
35:b0:e2:4a:3c:3e:ae:f8:01:9f:52:90:33:07:2f:
4e:79:f0:ee:2b:6e:25:f9:db:21:dc:72:e5:16:4b:
04:3f:36:0e:26:73:aa:97:50:7a:6f:0f:04:94:00:
1f:62:94:cb:2d:29:0d:3b:5e:b5:c6:84:da:65:90:
be:1c:96:22:73:cb:60:ac:8e:01:68:7c:2d:26:5e:
5d:ec:c3:0e:ff:99:00:53:01:93:cc:18:aa:94:f3:
69:cf:29:dc:8a:8c:c6:4a:e0:6c:6e:d0:38:95:3c:
cd:43:6f:8c:a8:75:d0:4e:ce:65:40:41:32:5d:3f:
83:fc:49:3b:e5:59:44:b1:f3:4e:a9:05:32:86:cf:
6e:d6:2a:f3:3e:63:5f:23:ad:e7:ca:1e:d3:b1:30:
e1:ee:dc:80:aa:f7:a8:e7:1d:0c:55:ba:d7:9b:e7:
31:5a:37:9e:0a:55:df:16:fa:9f:e6:01:6f:c8:a1:
47:10:72:d5:fa:6b:2d:6c:48:67:dc:cc:1d:5a:6f:
27:f3:8f:6e:57:b1:ef:83:fa:c6:5b:8c:09:ab:f8:
32:39
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
65:14:3e:1a:17:ba:a2:19:da:76:c8:3f:0b:26:5b:a5:59:ee:
eb:eb:a3:58:56:bc:15:92:b2:fe:a4:cc:8c:f5:a7:53:98:78:
ee:50:d0:0b:32:68:50:d1:af:7e:6c:f5:fd:b3:02:03:5b:6d:
87:4c:89:99:19:af:18:ee:3c:d2:52:59:62:24:37:63:f0:df:
9c:bc:df:0c:dd:d4:8d:d8:cb:3f:d6:f9:45:2b:ca:e1:c1:b5:
c6:35:f2:5d:4e:e2:40:6c:63:6d:8a:29:b1:08:1d:b7:ba:f6:
62:61:b3:5d:a9:ff:f2:cb:04:ff:b7:f4:95:ff:86:78:e9:bc:
dd:6f:0a:0c:9b:25:17:2b:78:1e:51:cd:41:de:09:10:ae:6d:
04:4f:f4:af:6e:b5:e8:4f:c7:2d:cd:e8:c6:e2:ed:3e:bd:f0:
78:14:e4:6c:63:cc:2e:9f:f2:84:b0:89:f4:41:2b:23:6c:2c:
8e:d2:c2:85:2f:70:ed:83:ac:c9:a8:57:09:1d:74:48:af:17:
b6:64:6f:ed:22:f1:3a:96:19:f0:c6:4c:21:f9:e8:3c:9a:0b:
dc:86:ea:d2:2a:2f:1c:30:60:3d:13:cc:af:8d:05:04:64:e5:
4c:79:88:cf:9b:94:dc:8d:29:5c:07:b6:fe:b1:99:1e:b5:a4:
8b:a7:cb:15
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
viewk8scertslabs
root@controlplane:/etc/kubernetes/pki# ls -rtlh
total 60K
-rw------- 1 root root 1.7K Sep 22 23:00 ca.key
-rw-r--r-- 1 root root 1.1K Sep 22 23:00 ca.crt
-rw------- 1 root root 1.7K Sep 22 23:00 apiserver.key
-rw-r--r-- 1 root root 1.3K Sep 22 23:00 apiserver.crt
-rw------- 1 root root 1.7K Sep 22 23:00 apiserver-kubelet-client.key
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 apiserver-kubelet-client.crt
-rw------- 1 root root 1.7K Sep 22 23:00 front-proxy-ca.key
-rw-r--r-- 1 root root 1.1K Sep 22 23:00 front-proxy-ca.crt
-rw------- 1 root root 1.7K Sep 22 23:00 front-proxy-client.key
-rw-r--r-- 1 root root 1.1K Sep 22 23:00 front-proxy-client.crt
drwxr-xr-x 2 root root 4.0K Sep 22 23:00 etcd
-rw------- 1 root root 1.7K Sep 22 23:00 apiserver-etcd-client.key
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 apiserver-etcd-client.crt
-rw------- 1 root root 451 Sep 22 23:00 sa.pub
-rw------- 1 root root 1.7K Sep 22 23:00 sa.key
root@controlplane:/etc/kubernetes/pki# pwd
/etc/kubernetes/pki
root@controlplane:/etc/kubernetes/pki#
Identify the Certificate file used to authenticate kube-apiserver as a client to ETCD Server
root@controlplane:/etc/kubernetes/pki# ls -rlth apiserver-etcd-client.crt
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 apiserver-etcd-client.crt
root@controlplane:/etc/kubernetes/pki#
root@controlplane:/etc/kubernetes/pki# ls -rtlh apiserver-kubelet-client.key
-rw------- 1 root root 1.7K Sep 22 23:00 apiserver-kubelet-client.key
root@controlplane:/etc/kubernetes/pki#
root@controlplane:/etc/kubernetes/pki/etcd# ls -lrth
total 32K
-rw------- 1 root root 1.7K Sep 22 23:00 ca.key
-rw-r--r-- 1 root root 1.1K Sep 22 23:00 ca.crt
-rw------- 1 root root 1.7K Sep 22 23:00 server.key
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 server.crt
-rw------- 1 root root 1.7K Sep 22 23:00 peer.key
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 peer.crt
-rw------- 1 root root 1.7K Sep 22 23:00 healthcheck-client.key
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 healthcheck-client.crt
root@controlplane:/etc/kubernetes/pki/etcd#
root@controlplane:/etc/kubernetes/pki# ls -rtlh
total 60K
-rw------- 1 root root 1.7K Sep 22 23:00 ca.key
-rw-r--r-- 1 root root 1.1K Sep 22 23:00 ca.crt
-rw------- 1 root root 1.7K Sep 22 23:00 apiserver.key
-rw-r--r-- 1 root root 1.3K Sep 22 23:00 apiserver.crt
-rw------- 1 root root 1.7K Sep 22 23:00 apiserver-kubelet-client.key
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 apiserver-kubelet-client.crt
-rw------- 1 root root 1.7K Sep 22 23:00 front-proxy-ca.key
-rw-r--r-- 1 root root 1.1K Sep 22 23:00 front-proxy-ca.crt
-rw------- 1 root root 1.7K Sep 22 23:00 front-proxy-client.key
-rw-r--r-- 1 root root 1.1K Sep 22 23:00 front-proxy-client.crt
drwxr-xr-x 2 root root 4.0K Sep 22 23:00 etcd
-rw------- 1 root root 1.7K Sep 22 23:00 apiserver-etcd-client.key
-rw-r--r-- 1 root root 1.2K Sep 22 23:00 apiserver-etcd-client.crt
-rw------- 1 root root 451 Sep 22 23:00 sa.pub
-rw------- 1 root root 1.7K Sep 22 23:00 sa.key
root@controlplane:/etc/kubernetes/pki# openssl x509 -in apiserver.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 5024350321412119082 (0x45ba13ff46e39a2a)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = kubernetes
Validity
Not Before: Sep 22 23:00:32 2021 GMT
Not After : Sep 22 23:00:32 2022 GMT
Subject: CN = kube-apiserver
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:c0:88:39:19:19:fa:35:ab:b6:88:32:84:20:8f:
0b:73:e1:9f:4f:0c:99:78:ea:66:eb:28:05:1e:06:
f0:05:1f:a1:c2:8a:ed:75:c4:79:12:fe:3f:a5:d1:
0c:bb:9c:c2:81:2e:fb:c0:fe:9f:1e:a7:56:fb:fd:
75:4f:46:54:93:a4:fc:ed:6d:95:1d:e7:b2:10:05:
fb:02:e7:9b:9d:9c:f7:b8:68:32:84:a4:e5:38:29:
51:51:85:35:b0:45:49:76:9e:7a:09:4a:01:7f:59:
91:99:8e:2f:24:a4:12:1e:d5:df:2b:e3:f1:c9:5e:
72:4e:67:f9:ab:dc:a7:29:6e:c1:d9:47:70:69:51:
62:37:1b:c5:02:7e:b0:9a:26:df:05:bc:09:b9:fb:
7a:dc:d4:e7:07:7c:d8:1f:e7:da:81:3a:4c:c4:4f:
f7:06:c9:62:0b:3a:af:7a:8c:59:5f:10:6a:1b:4f:
c3:64:14:e0:75:b5:83:ff:f1:eb:5d:5d:91:f4:8f:
09:ab:a0:5a:2b:ca:66:d2:59:66:cd:73:94:9a:25:
9a:8f:ca:e5:c2:8f:59:88:1d:d0:a5:25:64:09:b3:
1a:e8:52:12:b1:43:f0:5d:00:a1:75:cb:07:2a:74:
4b:c2:95:ae:fe:92:8b:c7:95:d3:9c:2a:38:60:68:
d7:45
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Authority Key Identifier:
keyid:A9:72:4F:47:6F:40:07:63:76:67:D3:79:51:92:52:65:E1:C3:14:6D
X509v3 Subject Alternative Name:
DNS:controlplane, DNS:kubernetes, DNS:kubernetes.default, DNS:kubernetes.default.svc, DNS:kubernetes.default.svc.cluster.local, IP Address:10.96.0.1, IP Address:10.56.203.8
Signature Algorithm: sha256WithRSAEncryption
58:21:ea:22:32:18:21:a5:b0:0a:e9:1e:21:42:71:7f:ab:46:
49:58:7a:62:2f:7f:a9:5f:bf:a9:c1:69:09:b2:c0:62:ad:71:
0c:e5:f2:10:8b:2a:94:07:78:d9:7a:1a:b9:17:6b:93:33:ab:
24:cc:b2:9e:ab:2f:32:ea:36:40:f0:02:df:36:91:76:99:4a:
07:fc:44:06:8e:c5:07:d0:01:f5:78:9c:55:e3:79:58:56:a6:
25:63:82:67:ca:27:e7:86:13:06:5a:4a:ea:e7:d5:55:d5:8e:
82:a5:92:a5:a2:a5:9d:88:06:2c:cb:74:01:fd:f2:9c:6e:1e:
73:9e:8c:e0:fd:b6:0e:e1:cc:7b:2c:68:fa:34:89:97:89:3e:
bd:7c:37:6a:6e:28:3f:50:cc:25:7b:94:84:18:b5:85:d2:3f:
54:b3:54:15:68:c4:5f:36:6a:19:49:f1:2e:3b:a6:94:b7:12:
97:d1:27:2e:08:12:48:71:1a:8d:aa:b8:f5:70:7f:83:43:27:
be:88:26:7a:09:b3:3b:a9:f0:c8:89:70:c6:49:cf:e8:75:4f:
e3:69:f8:9a:8a:8a:9c:89:54:1f:2b:19:3d:df:35:d2:fe:75:
0b:59:68:97:fa:f9:9a:5b:3b:e5:15:71:2d:6a:46:8f:4e:72:
07:c4:92:cc
root@controlplane:/etc/kubernetes/pki#
root@controlplane:/etc/kubernetes/pki# openssl x509 -in apiserver.crt -text -noout | grep -i "issuer"
Issuer: CN = kubernetes
root@controlplane:/etc/kubernetes/pki#
root@controlplane:/etc/kubernetes/pki# openssl x509 -in ca.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = kubernetes
Validity
Not Before: Sep 22 23:00:32 2021 GMT
Not After : Sep 20 23:00:32 2031 GMT
Subject: CN = kubernetes
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:9f:3c:af:c3:a2:5f:61:7d:a0:32:38:b3:e0:84:
2e:d8:a9:e3:db:40:74:ab:86:d2:02:33:bc:78:34:
0b:30:0e:73:f6:b8:af:17:cb:1c:64:29:69:c9:a2:
78:8a:a2:a5:b5:db:3f:b0:e8:33:2e:30:13:16:8a:
55:fe:9d:90:54:7f:d3:2e:7a:a8:2f:12:93:8b:44:
50:8e:24:f9:f0:e4:d4:1c:6d:f1:7f:a0:ad:f8:78:
40:2c:ad:8f:5e:71:02:08:11:55:ce:de:0f:33:7a:
fe:3e:cc:40:e6:ff:46:3d:21:77:e5:dc:0a:6e:a2:
f7:1f:e2:f8:e1:0e:e9:99:aa:d2:51:4e:b6:7e:83:
0e:6f:df:b6:dd:e8:6d:b8:4c:bf:d0:b0:ba:f2:5b:
3d:8d:63:ec:9f:e7:ba:44:14:9e:ac:52:22:e1:02:
ea:bc:63:b0:c8:6a:8b:00:a7:98:f7:d0:63:33:d9:
df:14:ca:c0:2f:ec:dd:27:3a:51:47:01:5c:7b:02:
27:76:32:83:24:6a:13:f6:9a:89:f3:e5:d8:40:3f:
9f:3e:5e:40:e5:22:38:2c:9a:dc:d2:2e:d6:56:24:
c3:a3:61:4b:57:c1:09:ec:89:95:ca:1d:97:06:14:
ad:6c:ad:a6:21:03:25:48:94:92:d4:4c:7e:f6:27:
9c:a1
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment, Certificate Sign
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
A9:72:4F:47:6F:40:07:63:76:67:D3:79:51:92:52:65:E1:C3:14:6D
Signature Algorithm: sha256WithRSAEncryption
42:e0:22:33:fc:7a:21:00:94:e5:66:7b:f7:59:27:42:3a:c5:
4f:e8:54:90:3a:7d:24:f1:29:5f:ed:e1:04:ff:e0:e5:cf:75:
be:46:f0:90:2b:97:c5:cd:10:20:8c:95:a6:ee:b5:29:81:e7:
d7:81:e7:89:09:02:97:a3:6f:c4:33:bd:03:fa:49:a7:1d:0f:
47:d1:a4:58:af:5c:22:4c:71:e2:89:a0:6d:39:bf:27:60:89:
42:7d:74:7d:68:b6:19:b2:28:90:b5:d6:57:e5:be:31:a6:55:
11:b6:7a:35:21:38:09:f3:cb:93:09:12:f1:42:c6:d3:78:33:
05:05:55:b1:a1:c7:1b:3d:71:af:5a:c9:6f:ef:e0:44:52:73:
49:92:14:11:ae:49:92:b2:40:b1:85:20:88:12:82:5d:bc:c5:
28:ca:c5:03:23:30:10:3e:ea:b6:44:3d:dc:90:e4:7d:17:35:
d0:35:f4:55:a0:0b:50:13:c2:11:8b:5f:21:ae:48:11:b8:52:
e9:f8:25:c2:d1:1a:f5:6c:6f:91:31:5b:aa:c8:79:e2:ec:f0:
29:d9:d4:c0:b3:f0:fc:bb:d7:e8:be:ca:ad:da:82:51:9b:75:
60:45:0f:68:29:0b:e3:f4:1e:b8:8b:6e:2e:18:ea:48:98:c7:
50:06:43:62
root@controlplane:/etc/kubernetes/pki#
root@controlplane:/etc/kubernetes/pki/etcd# openssl x509 -in server.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 3888003370887390627 (0x35f4f6775f43a5a3)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = etcd-ca
Validity
Not Before: Sep 22 23:00:34 2021 GMT
Not After : Sep 22 23:00:34 2022 GMT
Subject: CN = controlplane
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:a7:7b:fb:12:fa:e8:20:66:00:46:2c:36:0a:6d:
66:2f:d1:b0:41:76:da:6b:35:5e:c0:82:cb:ba:32:
b2:46:1d:1d:d6:44:5e:34:9c:fe:56:a1:72:ee:29:
f0:91:ea:22:4c:6c:2e:91:59:ff:88:8e:0b:ef:89:
2c:8b:b5:e5:4d:ee:bf:79:ea:50:49:c0:fc:8b:f1:
33:11:25:b6:ef:e7:aa:55:2c:83:40:b4:64:1e:a3:
7c:a5:61:6a:d9:e7:87:2b:a3:4f:35:74:5c:c4:84:
99:20:9b:ae:51:d5:71:cc:a3:84:c8:71:83:d5:1e:
5e:af:c6:46:e3:f3:3f:5a:ae:c8:b5:8e:cf:7f:a5:
2b:64:96:ce:93:8d:6f:a7:1c:d7:7e:91:5c:7a:e7:
5f:44:23:52:9e:66:15:81:93:34:19:6f:89:94:76:
48:98:25:56:73:12:3d:a9:3b:b6:e1:23:ad:70:df:
50:d9:9d:a1:39:18:75:94:1c:38:29:25:1e:41:30:
ad:ec:8d:0a:44:07:ec:27:d7:31:68:6e:9b:25:dd:
c7:b6:74:25:64:55:94:b5:ea:e3:f4:54:ec:96:49:
33:18:ee:59:3f:3e:7d:ce:78:8b:8b:39:37:6e:13:
a3:77:ef:0b:77:bf:90:8c:eb:1d:4b:f9:2e:fe:a7:
14:6f
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Authority Key Identifier:
keyid:49:94:05:BA:D9:64:3B:11:41:D9:1D:3A:0D:DF:1A:9C:DC:63:38:2F
X509v3 Subject Alternative Name:
DNS:controlplane, DNS:localhost, IP Address:10.56.203.8, IP Address:127.0.0.1, IP Address:0:0:0:0:0:0:0:1
Signature Algorithm: sha256WithRSAEncryption
21:bb:d7:25:c3:ef:3f:2c:ea:ff:f2:91:db:e1:12:e4:c6:8d:
02:42:02:74:37:a3:a3:0a:2d:b3:a6:52:71:02:d9:5f:0d:22:
6c:d9:49:ce:ec:70:81:c7:dc:b9:0a:0a:80:fb:59:72:6a:af:
1b:7f:00:2b:16:d0:d9:65:1f:40:5a:a2:ca:e1:2b:3d:24:68:
90:df:88:18:03:87:5e:c4:3b:ae:58:3b:16:34:39:18:67:1a:
e1:71:9b:8b:02:9b:93:d2:d0:7f:a9:33:c1:11:23:e5:30:34:
04:31:87:4b:b5:fe:41:c6:b8:86:2c:33:0d:9c:09:11:fc:a3:
35:fd:3a:d0:6b:c8:ec:ac:a7:c4:d6:3a:2e:51:9b:2a:3d:89:
ee:ae:56:cf:1b:51:f1:78:57:58:2f:99:86:6c:e1:c5:9b:e2:
85:e4:8f:30:cd:e8:07:6b:9b:b5:fb:62:93:38:1d:52:ba:2d:
85:80:b8:df:b3:c3:bc:22:fb:c0:b2:35:8f:df:c2:d3:77:d0:
4d:43:5d:66:08:dd:19:b1:3a:bf:49:f5:15:e1:82:7a:6b:38:
e1:f0:40:d1:24:e1:3e:ea:f6:a2:e4:f0:fd:5f:11:76:97:c0:
4d:17:12:b8:dd:09:0f:c8:6e:6f:c9:a6:d5:f2:1b:0c:6a:6d:
a9:11:a3:cc
root@controlplane:/etc/kubernetes/pki/etcd#
root@controlplane:/etc/kubernetes/pki/etcd# openssl x509 -in ../apiserver.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 5024350321412119082 (0x45ba13ff46e39a2a)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = kubernetes
Validity
Not Before: Sep 22 23:00:32 2021 GMT
Not After : Sep 22 23:00:32 2022 GMT
Subject: CN = kube-apiserver
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:c0:88:39:19:19:fa:35:ab:b6:88:32:84:20:8f:
0b:73:e1:9f:4f:0c:99:78:ea:66:eb:28:05:1e:06:
f0:05:1f:a1:c2:8a:ed:75:c4:79:12:fe:3f:a5:d1:
0c:bb:9c:c2:81:2e:fb:c0:fe:9f:1e:a7:56:fb:fd:
75:4f:46:54:93:a4:fc:ed:6d:95:1d:e7:b2:10:05:
fb:02:e7:9b:9d:9c:f7:b8:68:32:84:a4:e5:38:29:
51:51:85:35:b0:45:49:76:9e:7a:09:4a:01:7f:59:
91:99:8e:2f:24:a4:12:1e:d5:df:2b:e3:f1:c9:5e:
72:4e:67:f9:ab:dc:a7:29:6e:c1:d9:47:70:69:51:
62:37:1b:c5:02:7e:b0:9a:26:df:05:bc:09:b9:fb:
7a:dc:d4:e7:07:7c:d8:1f:e7:da:81:3a:4c:c4:4f:
f7:06:c9:62:0b:3a:af:7a:8c:59:5f:10:6a:1b:4f:
c3:64:14:e0:75:b5:83:ff:f1:eb:5d:5d:91:f4:8f:
09:ab:a0:5a:2b:ca:66:d2:59:66:cd:73:94:9a:25:
9a:8f:ca:e5:c2:8f:59:88:1d:d0:a5:25:64:09:b3:
1a:e8:52:12:b1:43:f0:5d:00:a1:75:cb:07:2a:74:
4b:c2:95:ae:fe:92:8b:c7:95:d3:9c:2a:38:60:68:
d7:45
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Authority Key Identifier:
keyid:A9:72:4F:47:6F:40:07:63:76:67:D3:79:51:92:52:65:E1:C3:14:6D
X509v3 Subject Alternative Name:
DNS:controlplane, DNS:kubernetes, DNS:kubernetes.default, DNS:kubernetes.default.svc, DNS:kubernetes.default.svc.cluster.local, IP Address:10.96.0.1, IP Address:10.56.203.8
Signature Algorithm: sha256WithRSAEncryption
58:21:ea:22:32:18:21:a5:b0:0a:e9:1e:21:42:71:7f:ab:46:
49:58:7a:62:2f:7f:a9:5f:bf:a9:c1:69:09:b2:c0:62:ad:71:
0c:e5:f2:10:8b:2a:94:07:78:d9:7a:1a:b9:17:6b:93:33:ab:
24:cc:b2:9e:ab:2f:32:ea:36:40:f0:02:df:36:91:76:99:4a:
07:fc:44:06:8e:c5:07:d0:01:f5:78:9c:55:e3:79:58:56:a6:
25:63:82:67:ca:27:e7:86:13:06:5a:4a:ea:e7:d5:55:d5:8e:
82:a5:92:a5:a2:a5:9d:88:06:2c:cb:74:01:fd:f2:9c:6e:1e:
73:9e:8c:e0:fd:b6:0e:e1:cc:7b:2c:68:fa:34:89:97:89:3e:
bd:7c:37:6a:6e:28:3f:50:cc:25:7b:94:84:18:b5:85:d2:3f:
54:b3:54:15:68:c4:5f:36:6a:19:49:f1:2e:3b:a6:94:b7:12:
97:d1:27:2e:08:12:48:71:1a:8d:aa:b8:f5:70:7f:83:43:27:
be:88:26:7a:09:b3:3b:a9:f0:c8:89:70:c6:49:cf:e8:75:4f:
e3:69:f8:9a:8a:8a:9c:89:54:1f:2b:19:3d:df:35:d2:fe:75:
0b:59:68:97:fa:f9:9a:5b:3b:e5:15:71:2d:6a:46:8f:4e:72:
07:c4:92:cc
root@controlplane:/etc/kubernetes/pki/etcd#
root@controlplane:/etc/kubernetes/pki/etcd# openssl x509 -in ../ca.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = kubernetes
Validity
Not Before: Sep 22 23:00:32 2021 GMT
Not After : Sep 20 23:00:32 2031 GMT
Subject: CN = kubernetes
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:9f:3c:af:c3:a2:5f:61:7d:a0:32:38:b3:e0:84:
2e:d8:a9:e3:db:40:74:ab:86:d2:02:33:bc:78:34:
0b:30:0e:73:f6:b8:af:17:cb:1c:64:29:69:c9:a2:
78:8a:a2:a5:b5:db:3f:b0:e8:33:2e:30:13:16:8a:
55:fe:9d:90:54:7f:d3:2e:7a:a8:2f:12:93:8b:44:
50:8e:24:f9:f0:e4:d4:1c:6d:f1:7f:a0:ad:f8:78:
40:2c:ad:8f:5e:71:02:08:11:55:ce:de:0f:33:7a:
fe:3e:cc:40:e6:ff:46:3d:21:77:e5:dc:0a:6e:a2:
f7:1f:e2:f8:e1:0e:e9:99:aa:d2:51:4e:b6:7e:83:
0e:6f:df:b6:dd:e8:6d:b8:4c:bf:d0:b0:ba:f2:5b:
3d:8d:63:ec:9f:e7:ba:44:14:9e:ac:52:22:e1:02:
ea:bc:63:b0:c8:6a:8b:00:a7:98:f7:d0:63:33:d9:
df:14:ca:c0:2f:ec:dd:27:3a:51:47:01:5c:7b:02:
27:76:32:83:24:6a:13:f6:9a:89:f3:e5:d8:40:3f:
9f:3e:5e:40:e5:22:38:2c:9a:dc:d2:2e:d6:56:24:
c3:a3:61:4b:57:c1:09:ec:89:95:ca:1d:97:06:14:
ad:6c:ad:a6:21:03:25:48:94:92:d4:4c:7e:f6:27:
9c:a1
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment, Certificate Sign
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
A9:72:4F:47:6F:40:07:63:76:67:D3:79:51:92:52:65:E1:C3:14:6D
Signature Algorithm: sha256WithRSAEncryption
42:e0:22:33:fc:7a:21:00:94:e5:66:7b:f7:59:27:42:3a:c5:
4f:e8:54:90:3a:7d:24:f1:29:5f:ed:e1:04:ff:e0:e5:cf:75:
be:46:f0:90:2b:97:c5:cd:10:20:8c:95:a6:ee:b5:29:81:e7:
d7:81:e7:89:09:02:97:a3:6f:c4:33:bd:03:fa:49:a7:1d:0f:
47:d1:a4:58:af:5c:22:4c:71:e2:89:a0:6d:39:bf:27:60:89:
42:7d:74:7d:68:b6:19:b2:28:90:b5:d6:57:e5:be:31:a6:55:
11:b6:7a:35:21:38:09:f3:cb:93:09:12:f1:42:c6:d3:78:33:
05:05:55:b1:a1:c7:1b:3d:71:af:5a:c9:6f:ef:e0:44:52:73:
49:92:14:11:ae:49:92:b2:40:b1:85:20:88:12:82:5d:bc:c5:
28:ca:c5:03:23:30:10:3e:ea:b6:44:3d:dc:90:e4:7d:17:35:
d0:35:f4:55:a0:0b:50:13:c2:11:8b:5f:21:ae:48:11:b8:52:
e9:f8:25:c2:d1:1a:f5:6c:6f:91:31:5b:aa:c8:79:e2:ec:f0:
29:d9:d4:c0:b3:f0:fc:bb:d7:e8:be:ca:ad:da:82:51:9b:75:
60:45:0f:68:29:0b:e3:f4:1e:b8:8b:6e:2e:18:ea:48:98:c7:
50:06:43:62
root@controlplane:/etc/kubernetes/pki/etcd#
getcsr
apiVersion: certificates.k8s.io/v1beta1
kind: CertificateSigningRequest
metadata:
name: bharath
spec:
groups:
- system:authenticated
usages:
- digital signature
- key encipherment
- server auth
request:
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1Z6Q0NBVDhDQVFBd0VqRVFNQTRHQTFVRUF3d0hZbWhoY21GMGFEQ0NBU0l3RFFZSktvWklodmNOQVFFQgpCUUFEZ2dFUEFEQ0NBUW9DZ2dFQkFPZ0tPR1UvUU9nTlRoeW1ucTl4VzBwREZSdnk0UG5uUERkYmF2RExIaTZnCjQ3dWpjYnFWY3MyYmdHbWlNdWlhTFQzV01YaVB4eFRjWXFKZDYvSGEyc1hBbXZLQUtVZTVpNUJRM093cTNrVncKbnBFN2xDczVOWWRzT25XYWVPRnBVbzJQMno0eDEzYzBPY2UxRms2UjNwZDdaSzlReWxqVEVxeVJhZ2ZVSEo0TQowak04V21mRHRmTXdWTlRRQzErYjVUdmRINmxhSTJMeXhjRFFzS3pYMUdLNW5WTDNaeS84NEM1NUlYL0Q4QTRNCnBxaVJtSXV1QTV3U0dhRnV5bEpGdGFXc2g0WHVpTytoRHdHNU8wcVdOeDkzaDBEZkFkb0JmZHVDb0k3RjdQU3oKcEtGQnBZdnFzc3hZcWJOTnJJRVhxZ3k4MUF1SU41VG83Wi9PUGYwb0Q2Y0NBd0VBQWFBQU1BMEdDU3FHU0liMwpEUUVCQ3dVQUE0SUJBUUJGcXFxYkJsOXFqWWhZTm1BTCtKb0NxSFozUTF2Qnpoa1owNWJnb1NPVUxVTHBNRUYyCmlnZ2JvSlRxQWY5NmU0OVlDRE1vaUlWUUg1K2JIT0hzMDBpRzFFK0FscEkwNVNGczVXRkh6bDFSMFJqdmpxWnYKcm1UcjFhWWpGeUh4dHBseGdqNnowQy8vYVZreEI1NnY2UklCQ0xLUkwzTmRUaWdHcE4rc2xTNmVtRjNic0lrbwp6T3VHYUg5TElSTllVL3BuRnJBcFpCU25vWElGa2M4WHRwS29IakttMDVmOUZZMlJseHhHdVl5bjZ0c2o2WGNkCnhsM1owWXI3cGoyWWVJdS9sWXNXcGdIalZsWHFZbVpIQWJVL1VwTll3ZzR3ZVRNRHVUWmQ0YUwwRVpQcGc2clkKKzFEckdHODFaeDZWbUhXa2xWTXdDUDkvQXZ2VlhqaWlHdVNBCi0tLS0tRU5EIENFUlRJRklDQVRFIFJFUVVFU1QtLS0tLQo=
k8scertAPI
Certificate workflow and API
1. API Object: Create CertificateSigningRequest Object
2. Review Requests
3. Approve Requests
Example:
------------>
1. A user first creates a key. and then generates a certificate signing request with his name on it.
MacBook-Pro:6.Security bharathdasaraju$ cd generate_tls_for_kubernetes/
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl genrsa -out bharath.key 2048
Generating RSA private key, 2048 bit long modulus
..................................+++
...............+++
e is 65537 (0x10001)
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ openssl req -new -key bharath.key -subj "/CN=bharath" -out bharath.csr
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ ls
admin.crt admin.key apiserver.csr bharath.csr ca.crt ca.key openssl-apiserver.conf
admin.csr apiserver.crt apiserver.key bharath.key ca.csr ca.srl
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
2. Then sends the request to the administrator. the administrator takes the key and creates a "CertificateSigningRequest" object.
The "CertificateSigningRequest" is created like any other kubernetes object using a manifest file with the usual fields.
The kind is "CertificateSigningRequest" under the spec section,
specify the groups the user should be part of and list the usages of the account as list of strings.
the request filed is where you specify the certificate signing request sent by the user.
But you wont specify as plain text, instead it must be encoded using the base64 command(as below) then move the encoded text into the requeast field.
and then submit the request.
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$ cat bharath.csr | base64
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1Z6Q0NBVDhDQVFBd0VqRVFNQTRHQTFVRUF3d0hZbWhoY21GMGFEQ0NBU0l3RFFZSktvWklodmNOQVFFQgpCUUFEZ2dFUEFEQ0NBUW9DZ2dFQkFPZ0tPR1UvUU9nTlRoeW1ucTl4VzBwREZSdnk0UG5uUERkYmF2RExIaTZnCjQ3dWpjYnFWY3MyYmdHbWlNdWlhTFQzV01YaVB4eFRjWXFKZDYvSGEyc1hBbXZLQUtVZTVpNUJRM093cTNrVncKbnBFN2xDczVOWWRzT25XYWVPRnBVbzJQMno0eDEzYzBPY2UxRms2UjNwZDdaSzlReWxqVEVxeVJhZ2ZVSEo0TQowak04V21mRHRmTXdWTlRRQzErYjVUdmRINmxhSTJMeXhjRFFzS3pYMUdLNW5WTDNaeS84NEM1NUlYL0Q4QTRNCnBxaVJtSXV1QTV3U0dhRnV5bEpGdGFXc2g0WHVpTytoRHdHNU8wcVdOeDkzaDBEZkFkb0JmZHVDb0k3RjdQU3oKcEtGQnBZdnFzc3hZcWJOTnJJRVhxZ3k4MUF1SU41VG83Wi9PUGYwb0Q2Y0NBd0VBQWFBQU1BMEdDU3FHU0liMwpEUUVCQ3dVQUE0SUJBUUJGcXFxYkJsOXFqWWhZTm1BTCtKb0NxSFozUTF2Qnpoa1owNWJnb1NPVUxVTHBNRUYyCmlnZ2JvSlRxQWY5NmU0OVlDRE1vaUlWUUg1K2JIT0hzMDBpRzFFK0FscEkwNVNGczVXRkh6bDFSMFJqdmpxWnYKcm1UcjFhWWpGeUh4dHBseGdqNnowQy8vYVZreEI1NnY2UklCQ0xLUkwzTmRUaWdHcE4rc2xTNmVtRjNic0lrbwp6T3VHYUg5TElSTllVL3BuRnJBcFpCU25vWElGa2M4WHRwS29IakttMDVmOUZZMlJseHhHdVl5bjZ0c2o2WGNkCnhsM1owWXI3cGoyWWVJdS9sWXNXcGdIalZsWHFZbVpIQWJVL1VwTll3ZzR3ZVRNRHVUWmQ0YUwwRVpQcGc2clkKKzFEckdHODFaeDZWbUhXa2xWTXdDUDkvQXZ2VlhqaWlHdVNBCi0tLS0tRU5EIENFUlRJRklDQVRFIFJFUVVFU1QtLS0tLQo=
MacBook-Pro:generate_tls_for_kubernetes bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl apply -f CertificateSigningRequest.yaml
Warning: certificates.k8s.io/v1beta1 CertificateSigningRequest is deprecated in v1.19+, unavailable in v1.22+; use certificates.k8s.io/v1 CertificateSigningRequest
certificatesigningrequest.certificates.k8s.io/bharath created
MacBook-Pro:6.Security bharathdasaraju$ kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
bharath 11s kubernetes.io/legacy-unknown minikube-user Pending
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
bharath 11s kubernetes.io/legacy-unknown minikube-user Pending
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl certificate approve bharath
certificatesigningrequest.certificates.k8s.io/bharath approved
MacBook-Pro:6.Security bharathdasaraju$ kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
bharath 51s kubernetes.io/legacy-unknown minikube-user Approved,Issued
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl get csr bharath -o yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"certificates.k8s.io/v1beta1","kind":"CertificateSigningRequest","metadata":{"annotations":{},"name":"bharath"},"spec":{"groups":["system:authenticated"],"request":"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1Z6Q0NBVDhDQVFBd0VqRVFNQTRHQTFVRUF3d0hZbWhoY21GMGFEQ0NBU0l3RFFZSktvWklodmNOQVFFQgpCUUFEZ2dFUEFEQ0NBUW9DZ2dFQkFPZ0tPR1UvUU9nTlRoeW1ucTl4VzBwREZSdnk0UG5uUERkYmF2RExIaTZnCjQ3dWpjYnFWY3MyYmdHbWlNdWlhTFQzV01YaVB4eFRjWXFKZDYvSGEyc1hBbXZLQUtVZTVpNUJRM093cTNrVncKbnBFN2xDczVOWWRzT25XYWVPRnBVbzJQMno0eDEzYzBPY2UxRms2UjNwZDdaSzlReWxqVEVxeVJhZ2ZVSEo0TQowak04V21mRHRmTXdWTlRRQzErYjVUdmRINmxhSTJMeXhjRFFzS3pYMUdLNW5WTDNaeS84NEM1NUlYL0Q4QTRNCnBxaVJtSXV1QTV3U0dhRnV5bEpGdGFXc2g0WHVpTytoRHdHNU8wcVdOeDkzaDBEZkFkb0JmZHVDb0k3RjdQU3oKcEtGQnBZdnFzc3hZcWJOTnJJRVhxZ3k4MUF1SU41VG83Wi9PUGYwb0Q2Y0NBd0VBQWFBQU1BMEdDU3FHU0liMwpEUUVCQ3dVQUE0SUJBUUJGcXFxYkJsOXFqWWhZTm1BTCtKb0NxSFozUTF2Qnpoa1owNWJnb1NPVUxVTHBNRUYyCmlnZ2JvSlRxQWY5NmU0OVlDRE1vaUlWUUg1K2JIT0hzMDBpRzFFK0FscEkwNVNGczVXRkh6bDFSMFJqdmpxWnYKcm1UcjFhWWpGeUh4dHBseGdqNnowQy8vYVZreEI1NnY2UklCQ0xLUkwzTmRUaWdHcE4rc2xTNmVtRjNic0lrbwp6T3VHYUg5TElSTllVL3BuRnJBcFpCU25vWElGa2M4WHRwS29IakttMDVmOUZZMlJseHhHdVl5bjZ0c2o2WGNkCnhsM1owWXI3cGoyWWVJdS9sWXNXcGdIalZsWHFZbVpIQWJVL1VwTll3ZzR3ZVRNRHVUWmQ0YUwwRVpQcGc2clkKKzFEckdHODFaeDZWbUhXa2xWTXdDUDkvQXZ2VlhqaWlHdVNBCi0tLS0tRU5EIENFUlRJRklDQVRFIFJFUVVFU1QtLS0tLQo=","usages":["digital signature","key encipherment","server auth"]}}
creationTimestamp: "2021-09-22T23:53:45Z"
managedFields:
- apiVersion: certificates.k8s.io/v1beta1
fieldsType: FieldsV1
fieldsV1:
f:metadata:
f:annotations:
.: {}
f:kubectl.kubernetes.io/last-applied-configuration: {}
f:spec:
f:groups: {}
f:request: {}
f:signerName: {}
f:usages: {}
manager: kubectl-client-side-apply
operation: Update
time: "2021-09-22T23:53:45Z"
- apiVersion: certificates.k8s.io/v1
fieldsType: FieldsV1
fieldsV1:
f:status:
f:certificate: {}
manager: kube-controller-manager
operation: Update
time: "2021-09-22T23:54:33Z"
- apiVersion: certificates.k8s.io/v1
fieldsType: FieldsV1
fieldsV1:
f:status:
f:conditions:
.: {}
k:{"type":"Approved"}:
.: {}
f:lastTransitionTime: {}
f:lastUpdateTime: {}
f:message: {}
f:reason: {}
f:status: {}
f:type: {}
manager: kubectl
operation: Update
time: "2021-09-22T23:54:33Z"
name: bharath
resourceVersion: "121875"
uid: dcdbbadd-fb6a-489f-86dc-47dd868b9a33
spec:
groups:
- system:masters
- system:authenticated
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1Z6Q0NBVDhDQVFBd0VqRVFNQTRHQTFVRUF3d0hZbWhoY21GMGFEQ0NBU0l3RFFZSktvWklodmNOQVFFQgpCUUFEZ2dFUEFEQ0NBUW9DZ2dFQkFPZ0tPR1UvUU9nTlRoeW1ucTl4VzBwREZSdnk0UG5uUERkYmF2RExIaTZnCjQ3dWpjYnFWY3MyYmdHbWlNdWlhTFQzV01YaVB4eFRjWXFKZDYvSGEyc1hBbXZLQUtVZTVpNUJRM093cTNrVncKbnBFN2xDczVOWWRzT25XYWVPRnBVbzJQMno0eDEzYzBPY2UxRms2UjNwZDdaSzlReWxqVEVxeVJhZ2ZVSEo0TQowak04V21mRHRmTXdWTlRRQzErYjVUdmRINmxhSTJMeXhjRFFzS3pYMUdLNW5WTDNaeS84NEM1NUlYL0Q4QTRNCnBxaVJtSXV1QTV3U0dhRnV5bEpGdGFXc2g0WHVpTytoRHdHNU8wcVdOeDkzaDBEZkFkb0JmZHVDb0k3RjdQU3oKcEtGQnBZdnFzc3hZcWJOTnJJRVhxZ3k4MUF1SU41VG83Wi9PUGYwb0Q2Y0NBd0VBQWFBQU1BMEdDU3FHU0liMwpEUUVCQ3dVQUE0SUJBUUJGcXFxYkJsOXFqWWhZTm1BTCtKb0NxSFozUTF2Qnpoa1owNWJnb1NPVUxVTHBNRUYyCmlnZ2JvSlRxQWY5NmU0OVlDRE1vaUlWUUg1K2JIT0hzMDBpRzFFK0FscEkwNVNGczVXRkh6bDFSMFJqdmpxWnYKcm1UcjFhWWpGeUh4dHBseGdqNnowQy8vYVZreEI1NnY2UklCQ0xLUkwzTmRUaWdHcE4rc2xTNmVtRjNic0lrbwp6T3VHYUg5TElSTllVL3BuRnJBcFpCU25vWElGa2M4WHRwS29IakttMDVmOUZZMlJseHhHdVl5bjZ0c2o2WGNkCnhsM1owWXI3cGoyWWVJdS9sWXNXcGdIalZsWHFZbVpIQWJVL1VwTll3ZzR3ZVRNRHVUWmQ0YUwwRVpQcGc2clkKKzFEckdHODFaeDZWbUhXa2xWTXdDUDkvQXZ2VlhqaWlHdVNBCi0tLS0tRU5EIENFUlRJRklDQVRFIFJFUVVFU1QtLS0tLQo=
signerName: kubernetes.io/legacy-unknown
usages:
- digital signature
- key encipherment
- server auth
username: minikube-user
status:
certificate: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1akNDQWM2Z0F3SUJBZ0lRWVdpS3cveHNkVkpVT09pMTBBZU9LekFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwdGFXNXBhM1ZpWlVOQk1CNFhEVEl4TURreU1qSXpORGt6TTFvWERUSXlNRGt5TWpJegpORGt6TTFvd0VqRVFNQTRHQTFVRUF4TUhZbWhoY21GMGFEQ0NBU0l3RFFZSktvWklodmNOQVFFQkJRQURnZ0VQCkFEQ0NBUW9DZ2dFQkFPZ0tPR1UvUU9nTlRoeW1ucTl4VzBwREZSdnk0UG5uUERkYmF2RExIaTZnNDd1amNicVYKY3MyYmdHbWlNdWlhTFQzV01YaVB4eFRjWXFKZDYvSGEyc1hBbXZLQUtVZTVpNUJRM093cTNrVnducEU3bENzNQpOWWRzT25XYWVPRnBVbzJQMno0eDEzYzBPY2UxRms2UjNwZDdaSzlReWxqVEVxeVJhZ2ZVSEo0TTBqTThXbWZECnRmTXdWTlRRQzErYjVUdmRINmxhSTJMeXhjRFFzS3pYMUdLNW5WTDNaeS84NEM1NUlYL0Q4QTRNcHFpUm1JdXUKQTV3U0dhRnV5bEpGdGFXc2g0WHVpTytoRHdHNU8wcVdOeDkzaDBEZkFkb0JmZHVDb0k3RjdQU3pwS0ZCcFl2cQpzc3hZcWJOTnJJRVhxZ3k4MUF1SU41VG83Wi9PUGYwb0Q2Y0NBd0VBQWFNMU1ETXdEZ1lEVlIwUEFRSC9CQVFECkFnV2dNQk1HQTFVZEpRUU1NQW9HQ0NzR0FRVUZCd01CTUF3R0ExVWRFd0VCL3dRQ01BQXdEUVlKS29aSWh2Y04KQVFFTEJRQURnZ0VCQUZ2NVE5QXRaR2QySnVwY3N5a29OZ3N0ODNmKzFjc1FYbjJtN1MxcWF3UnB0VVVFRDRiRwpyU0czUGRzeTVWZWxQQmlicHRiS0dXNitQU2xyc3lHRDRWZkJ6RWIzaVFGSWtiL1ltY1h0WVhKMEx2cjBqY1FHCjN5N01DbDMyYWR1MDJtSWNlcm5NZG1kekRlQUhENkg2YThqeG9oOEZvZktNNmlQdytyM3hYWWhxVmJyalFscnQKclZ2cDNwbE9qc0pSUW5pWnpMb3Y0UXRzNk02RHBySWlsditVUU9lMUZ5eXpuSCtaV2JwUmZMejJ6L0ZqT0ZvVgpCeXpaM0NmN1BxSEM0ZXFyZHF2U3VQdHhhK3VaNU1xWVlnRHN4NjRraEVqR0dkNHFlSVdpbHFQcWNuNG5USlRJCi82ZXhlVi9LaEwzc3lXaUN1TGJjWllqMnRQWDZ5WkN2UmNrPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
conditions:
- lastTransitionTime: "2021-09-22T23:54:33Z"
lastUpdateTime: "2021-09-22T23:54:33Z"
message: This CSR was approved by kubectl certificate approve.
reason: KubectlApprove
status: "True"
type: Approved
MacBook-Pro:6.Security bharathdasaraju$
So the issued certificate is as below:
----------------------------------------------------->
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1akNDQWM2Z0F3SUJBZ0lRWVdpS3cveHNkVkpVT09pMTBBZU9LekFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwdGFXNXBhM1ZpWlVOQk1CNFhEVEl4TURreU1qSXpORGt6TTFvWERUSXlNRGt5TWpJegpORGt6TTFvd0VqRVFNQTRHQTFVRUF4TUhZbWhoY21GMGFEQ0NBU0l3RFFZSktvWklodmNOQVFFQkJRQURnZ0VQCkFEQ0NBUW9DZ2dFQkFPZ0tPR1UvUU9nTlRoeW1ucTl4VzBwREZSdnk0UG5uUERkYmF2RExIaTZnNDd1amNicVYKY3MyYmdHbWlNdWlhTFQzV01YaVB4eFRjWXFKZDYvSGEyc1hBbXZLQUtVZTVpNUJRM093cTNrVnducEU3bENzNQpOWWRzT25XYWVPRnBVbzJQMno0eDEzYzBPY2UxRms2UjNwZDdaSzlReWxqVEVxeVJhZ2ZVSEo0TTBqTThXbWZECnRmTXdWTlRRQzErYjVUdmRINmxhSTJMeXhjRFFzS3pYMUdLNW5WTDNaeS84NEM1NUlYL0Q4QTRNcHFpUm1JdXUKQTV3U0dhRnV5bEpGdGFXc2g0WHVpTytoRHdHNU8wcVdOeDkzaDBEZkFkb0JmZHVDb0k3RjdQU3pwS0ZCcFl2cQpzc3hZcWJOTnJJRVhxZ3k4MUF1SU41VG83Wi9PUGYwb0Q2Y0NBd0VBQWFNMU1ETXdEZ1lEVlIwUEFRSC9CQVFECkFnV2dNQk1HQTFVZEpRUU1NQW9HQ0NzR0FRVUZCd01CTUF3R0ExVWRFd0VCL3dRQ01BQXdEUVlKS29aSWh2Y04KQVFFTEJRQURnZ0VCQUZ2NVE5QXRaR2QySnVwY3N5a29OZ3N0ODNmKzFjc1FYbjJtN1MxcWF3UnB0VVVFRDRiRwpyU0czUGRzeTVWZWxQQmlicHRiS0dXNitQU2xyc3lHRDRWZkJ6RWIzaVFGSWtiL1ltY1h0WVhKMEx2cjBqY1FHCjN5N01DbDMyYWR1MDJtSWNlcm5NZG1kekRlQUhENkg2YThqeG9oOEZvZktNNmlQdytyM3hYWWhxVmJyalFscnQKclZ2cDNwbE9qc0pSUW5pWnpMb3Y0UXRzNk02RHBySWlsditVUU9lMUZ5eXpuSCtaV2JwUmZMejJ6L0ZqT0ZvVgpCeXpaM0NmN1BxSEM0ZXFyZHF2U3VQdHhhK3VaNU1xWVlnRHN4NjRraEVqR0dkNHFlSVdpbHFQcWNuNG5USlRJCi82ZXhlVi9LaEwzc3lXaUN1TGJjWllqMnRQWDZ5WkN2UmNrPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
MacBook-Pro:6.Security bharathdasaraju$ echo "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1akNDQWM2Z0F3SUJBZ0lRWVdpS3cveHNkVkpVT09pMTBBZU9LekFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwdGFXNXBhM1ZpWlVOQk1CNFhEVEl4TURreU1qSXpORGt6TTFvWERUSXlNRGt5TWpJegpORGt6TTFvd0VqRVFNQTRHQTFVRUF4TUhZbWhoY21GMGFEQ0NBU0l3RFFZSktvWklodmNOQVFFQkJRQURnZ0VQCkFEQ0NBUW9DZ2dFQkFPZ0tPR1UvUU9nTlRoeW1ucTl4VzBwREZSdnk0UG5uUERkYmF2RExIaTZnNDd1amNicVYKY3MyYmdHbWlNdWlhTFQzV01YaVB4eFRjWXFKZDYvSGEyc1hBbXZLQUtVZTVpNUJRM093cTNrVnducEU3bENzNQpOWWRzT25XYWVPRnBVbzJQMno0eDEzYzBPY2UxRms2UjNwZDdaSzlReWxqVEVxeVJhZ2ZVSEo0TTBqTThXbWZECnRmTXdWTlRRQzErYjVUdmRINmxhSTJMeXhjRFFzS3pYMUdLNW5WTDNaeS84NEM1NUlYL0Q4QTRNcHFpUm1JdXUKQTV3U0dhRnV5bEpGdGFXc2g0WHVpTytoRHdHNU8wcVdOeDkzaDBEZkFkb0JmZHVDb0k3RjdQU3pwS0ZCcFl2cQpzc3hZcWJOTnJJRVhxZ3k4MUF1SU41VG83Wi9PUGYwb0Q2Y0NBd0VBQWFNMU1ETXdEZ1lEVlIwUEFRSC9CQVFECkFnV2dNQk1HQTFVZEpRUU1NQW9HQ0NzR0FRVUZCd01CTUF3R0ExVWRFd0VCL3dRQ01BQXdEUVlKS29aSWh2Y04KQVFFTEJRQURnZ0VCQUZ2NVE5QXRaR2QySnVwY3N5a29OZ3N0ODNmKzFjc1FYbjJtN1MxcWF3UnB0VVVFRDRiRwpyU0czUGRzeTVWZWxQQmlicHRiS0dXNitQU2xyc3lHRDRWZkJ6RWIzaVFGSWtiL1ltY1h0WVhKMEx2cjBqY1FHCjN5N01DbDMyYWR1MDJtSWNlcm5NZG1kekRlQUhENkg2YThqeG9oOEZvZktNNmlQdytyM3hYWWhxVmJyalFscnQKclZ2cDNwbE9qc0pSUW5pWnpMb3Y0UXRzNk02RHBySWlsditVUU9lMUZ5eXpuSCtaV2JwUmZMejJ6L0ZqT0ZvVgpCeXpaM0NmN1BxSEM0ZXFyZHF2U3VQdHhhK3VaNU1xWVlnRHN4NjRraEVqR0dkNHFlSVdpbHFQcWNuNG5USlRJCi82ZXhlVi9LaEwzc3lXaUN1TGJjWllqMnRQWDZ5WkN2UmNrPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==" | base64 --decode
-----BEGIN CERTIFICATE-----
MIIC5jCCAc6gAwIBAgIQYWiKw/xsdVJUOOi10AeOKzANBgkqhkiG9w0BAQsFADAV
MRMwEQYDVQQDEwptaW5pa3ViZUNBMB4XDTIxMDkyMjIzNDkzM1oXDTIyMDkyMjIz
NDkzM1owEjEQMA4GA1UEAxMHYmhhcmF0aDCCASIwDQYJKoZIhvcNAQEBBQADggEP
ADCCAQoCggEBAOgKOGU/QOgNThymnq9xW0pDFRvy4PnnPDdbavDLHi6g47ujcbqV
cs2bgGmiMuiaLT3WMXiPxxTcYqJd6/Ha2sXAmvKAKUe5i5BQ3Owq3kVwnpE7lCs5
NYdsOnWaeOFpUo2P2z4x13c0Oce1Fk6R3pd7ZK9QyljTEqyRagfUHJ4M0jM8WmfD
tfMwVNTQC1+b5TvdH6laI2LyxcDQsKzX1GK5nVL3Zy/84C55IX/D8A4MpqiRmIuu
A5wSGaFuylJFtaWsh4XuiO+hDwG5O0qWNx93h0DfAdoBfduCoI7F7PSzpKFBpYvq
ssxYqbNNrIEXqgy81AuIN5To7Z/OPf0oD6cCAwEAAaM1MDMwDgYDVR0PAQH/BAQD
AgWgMBMGA1UdJQQMMAoGCCsGAQUFBwMBMAwGA1UdEwEB/wQCMAAwDQYJKoZIhvcN
AQELBQADggEBAFv5Q9AtZGd2JupcsykoNgst83f+1csQXn2m7S1qawRptUUED4bG
rSG3Pdsy5VelPBibptbKGW6+PSlrsyGD4VfBzEb3iQFIkb/YmcXtYXJ0Lvr0jcQG
3y7MCl32adu02mIcernMdmdzDeAHD6H6a8jxoh8FofKM6iPw+r3xXYhqVbrjQlrt
rVvp3plOjsJRQniZzLov4Qts6M6DprIilv+UQOe1FyyznH+ZWbpRfLz2z/FjOFoV
ByzZ3Cf7PqHC4eqrdqvSuPtxa+uZ5MqYYgDsx64khEjGGd4qeIWilqPqcn4nTJTI
/6exeV/KhL3syWiCuLbcZYj2tPX6yZCvRck=
-----END CERTIFICATE-----
MacBook-Pro:6.Security bharathdasaraju$
Kube controlller-manager does all this certificate stuff :)
kube-controller-manager yaml file:
------------------------------------->
--cluster-signing-cert-file=/etc/kubernetes/pki/ca.crt
--cluster-signing-key-file=/etc/kubernetes/pki/ca.key
csruser
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
name: akshay
spec:
groups:
- system:authenticated
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1ZqQ0NBVDRDQVFBd0VURVBNQTBHQTFVRUF3d0dZV3R6YUdGNU1JSUJJakFOQmdrcWhraUc5dzBCQVFFRgpBQU9DQVE4QU1JSUJDZ0tDQVFFQXY4azZTTE9HVzcrV3JwUUhITnI2TGFROTJhVmQ1blNLajR6UEhsNUlJYVdlCmJ4RU9JYkNmRkhKKzlIOE1RaS9hbCswcEkwR2xpYnlmTXozL2lGSWF3eGVXNFA3bDJjK1g0L0lqOXZQVC9jU3UKMDAya2ZvV0xUUkpQbWtKaVVuQTRpSGxZNDdmYkpQZDhIRGFuWHM3bnFoenVvTnZLbWhwL2twZUVvaHd5MFRVMAo5bzdvcjJWb1hWZTVyUnNoMms4dzV2TlVPL3BBdEk4VkRydUhCYzRxaHM3MDI1ZTZTUXFDeHUyOHNhTDh1blJQCkR6V2ZsNVpLcTVpdlJNeFQrcUo0UGpBL2pHV2d6QVliL1hDQXRrRVJyNlMwak9XaEw1Q0ErVU1BQmd5a1c5emQKTmlXbnJZUEdqVWh1WjZBeWJ1VzMxMjRqdlFvbndRRUprNEdoayt2SU53SURBUUFCb0FBd0RRWUpLb1pJaHZjTgpBUUVMQlFBRGdnRUJBQi94dDZ2d2EweWZHZFpKZ1k2ZDRUZEFtN2ZiTHRqUE15OHByTi9WZEdxN25oVDNUUE5zCjEwRFFaVGN6T21hTjVTZmpTaVAvaDRZQzQ0QjhFMll5Szg4Z2lDaUVEWDNlaDFYZnB3bnlJMVBDVE1mYys3cWUKMkJZTGJWSitRY040MDU4YituK24wMy9oVkN4L1VRRFhvc2w4Z2hOaHhGck9zRUtuVExiWHRsK29jQ0RtN3I3UwpUYTFkbWtFWCtWUnFJYXFGSDd1dDJveHgxcHdCdnJEeGUvV2cybXNqdHJZUXJ3eDJmQnErQ2Z1dm1sVS9rME4rCml3MEFjbVJsMy9veTdqR3ptMXdqdTJvNG4zSDNKQ25SbE41SnIyQkZTcFVQU3dCL1lUZ1ZobHVMNmwwRERxS3MKNTdYcEYxcjZWdmJmbTRldkhDNnJCSnNiZmI2ZU1KejZPMUU9Ci0tLS0tRU5EIENFUlRJRklDQVRFIFJFUVVFU1QtLS0tLQo=
signerName: kubernetes.io/kube-apiserver-client
usages:
- client auth
k8scertlabs
A new member akshay joined our team. He requires access to our cluster. The Certificate Signing Request is at the /root location.
root@controlplane:~# ls -lrth
total 8.0K
-rw------- 1 root root 1.7K Sep 23 00:03 akshay.key
-rw-r--r-- 1 root root 887 Sep 23 00:03 akshay.csr
root@controlplane:~#
root@controlplane:~# cat akshay.csr | base64
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1ZqQ0NBVDRDQVFBd0VURVBN
QTBHQTFVRUF3d0dZV3R6YUdGNU1JSUJJakFOQmdrcWhraUc5dzBCQVFFRgpBQU9DQVE4QU1JSUJD
Z0tDQVFFQXBQTE5NcjBjUDZueVIrTmdmYVJ0UFNKemVIZXFXS21Ha21nMmk1NmRoQWFYCnlaNTFK
SVkwY0MyUWpXQ2o0ZTF5ZUJlUFRJWThPSWQ1QXdKcU92Y05JMzh1SWZ1WjVDNkhNV3ZXR2lOZmNj
ek0KeUVLTFhxMTVDSy91bUNSTDEwenBiOFdBVzkyS2tPY05xbENza1VnWWpZbWs4RkdwS2J6dUhw
bVdsVjdEcm9hLwpJSlVVRXN0NGcyN1JCRHVVNk1PVnRHMUMwMnpmd1UyeUxCSzFsMDgyV29NVno0
NzY3UWZsdWlIWmR5MEdaZUZMCjBHalpvYkxNelFRS0U3V0dGa3ZiUzdMaklRSVR4M0QwSEV1OUVE
NnFURHpyN3JUS005VTVrcXQ1VHBldHhqNnYKSWFhR2lrRmNLbnl4NExaOE9seVFDdlNFdlNOT2JO
blpSTkt1VTRHTXV3SURBUUFCb0FBd0RRWUpLb1pJaHZjTgpBUUVMQlFBRGdnRUJBQitORGFUZ1Y0
MnZ3R2lPbjRmT0lodlpkQ3o1WkQzbXlyL25kcHVWaFBwMTg5cTN0STI2CjhYUzBHUGY2aFlDV2g5
aGl5TWM0SGZUR3h2M1ZFYlU0WWFnVVczTnlCUHlKY0tCNXoyMEZVNWZramFRdmhUdkcKTmx6blgy
UURXRmtHY3RZb05uZjdwdFFkRldnUnVERklaSEZHN291OE84UCtBUE5iVlRpR1gyc05CaGFXVjJW
VApsVHVSZk5zQkNndlRvZDdIQ0F1Tzl4OExIbFVhdUNVYnV3STNvN3ZVYVpWanJVeVZscFd1MGFU
QlZ2OVNJWWNMCldrRmxxU0tGM0c4ektrelE0TGxyZEo3dnpjajVZVld6M2NkWjRtc1NJaDdWZ1dZ
L2lrYlpLKy9LVW9JdU9IY3oKL2VMQ0hDK2lNSGJiMzVqcjEyZkVBamdVK2hoTHlxdThZZms9Ci0t
LS0tRU5EIENFUlRJRklDQVRFIFJFUVVFU1QtLS0tLQo=
root@controlplane:~#
root@controlplane:~# ls -rtlh
total 12K
-rw------- 1 root root 1.7K Sep 23 00:03 akshay.key
-rw-r--r-- 1 root root 887 Sep 23 00:03 akshay.csr
-rw-r--r-- 1 root root 1.4K Sep 23 00:06 certificatesiging.yaml
root@controlplane:~# vim CertSigningRequest_user.yaml
root@controlplane:~# kubectl apply -f CertSigningRequest_user.yaml
certificatesigningrequest.certificates.k8s.io/akshay created
root@controlplane:~#
root@controlplane:~# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
akshay 48s kubernetes.io/kube-apiserver-client kubernetes-admin Pending
csr-7788z 16m kubernetes.io/kube-apiserver-client-kubelet system:node:controlplane Approved,Issued
root@controlplane:~#
root@controlplane:~# kubectl certificate approve akshay
certificatesigningrequest.certificates.k8s.io/akshay approved
root@controlplane:~# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
akshay 109s kubernetes.io/kube-apiserver-client kubernetes-admin Approved,Issued
csr-7788z 17m kubernetes.io/kube-apiserver-client-kubelet system:node:controlplane Approved,Issued
root@controlplane:~#
root@controlplane:~# kubectl get csr agent-smith -o yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
creationTimestamp: "2021-09-23T00:15:27Z"
managedFields:
- apiVersion: certificates.k8s.io/v1
fieldsType: FieldsV1
fieldsV1:
f:spec:
f:groups: {}
f:request: {}
f:signerName: {}
f:usages: {}
manager: kubectl-create
operation: Update
time: "2021-09-23T00:15:27Z"
name: agent-smith
resourceVersion: "1794"
uid: 8a739bc7-cc33-46b8-8208-5df6969917e7
spec:
groups:
- system:masters
- system:authenticated
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1dEQ0NBVUFDQVFBd0V6RVJNQThHQTFVRUF3d0libVYzTFhWelpYSXdnZ0VpTUEwR0NTcUdTSWIzRFFFQgpBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRRE8wV0pXK0RYc0FKU0lyanBObzV2UklCcGxuemcrNnhjOStVVndrS2kwCkxmQzI3dCsxZUVuT041TXVxOTlOZXZtTUVPbnJEVU8vdGh5VnFQMncyWE5JRFJYall5RjQwRmJtRCs1eld5Q0sKeTNCaWhoQjkzTUo3T3FsM1VUdlo4VEVMcXlhRGtuUmwvanYvU3hnWGtvazBBQlVUcFdNeDRCcFNpS2IwVSt0RQpJRjVueEF0dE1Wa0RQUTdOYmVaUkc0M2IrUVdsVkdSL3o2RFdPZkpuYmZlek90YUF5ZEdMVFpGQy93VHB6NTJrCkVjQ1hBd3FDaGpCTGt6MkJIUFI0Sjg5RDZYYjhrMzlwdTZqcHluZ1Y2dVAwdEliT3pwcU52MFkwcWRFWnB3bXcKajJxRUwraFpFV2trRno4MGxOTnR5VDVMeE1xRU5EQ25JZ3dDNEdaaVJHYnJBZ01CQUFHZ0FEQU5CZ2txaGtpRwo5dzBCQVFzRkFBT0NBUUVBUzlpUzZDMXV4VHVmNUJCWVNVN1FGUUhVemFsTnhBZFlzYU9SUlFOd0had0hxR2k0CmhPSzRhMnp5TnlpNDRPT2lqeWFENnRVVzhEU3hrcjhCTEs4S2czc3JSRXRKcWw1ckxaeTlMUlZyc0pnaEQ0Z1kKUDlOTCthRFJTeFJPVlNxQmFCMm5XZVlwTTVjSjVURjUzbGVzTlNOTUxRMisrUk1uakRRSjdqdVBFaWM4L2RoawpXcjJFVU02VWF3enlrcmRISW13VHYybWxNWTBSK0ROdFYxWWllKzBIOS9ZRWx0K0ZTR2poNUw1WVV2STFEcWl5CjRsM0UveTNxTDcxV2ZBY3VIM09zVnBVVW5RSVNNZFFzMHFXQ3NiRTU2Q0M1RGhQR1pJcFVibktVcEF3a2ErOEUKdndRMDdqRytocGtueG11RkFlWHhnVXdvZEFMYUo3anUvVERJY3c9PQotLS0tLUVORCBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0K
signerName: kubernetes.io/kube-apiserver-client
usages:
- digital signature
- key encipherment
- server auth
username: agent-x
status: {}
root@controlplane:~#
root@controlplane:~# kubectl certificate deny agent-smith
certificatesigningrequest.certificates.k8s.io/agent-smith denied
root@controlplane:~# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
agent-smith 106s kubernetes.io/kube-apiserver-client agent-x Denied
akshay 4m17s kubernetes.io/kube-apiserver-client kubernetes-admin Approved,Issued
csr-7788z 20m kubernetes.io/kube-apiserver-client-kubelet system:node:controlplane Approved,Issued
root@controlplane:~#
root@controlplane:~# kubectl delete csr agent-smith
certificatesigningrequest.certificates.k8s.io "agent-smith" deleted
root@controlplane:~#
kubeconfig1
apiVersion: v1
kind: Config
current-context: dev-user@google
clusters:
- name: my-kube-play
- name: development
- name: production
- name: staging
contexts:
- name: my-kube-admin@my-kube-play
- name: dev-user@google
- name: prod-user@production
- name: admin@development
users:
- name: my-kube-admin
- name: admin
- name: dev-user
- name: prod-user
kubeconfig2
apiVersion: v1
kind: Config
clusters:
- name: production
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://172.17.0.87:6443
- name: development
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://172.17.0.87:6443
- name: kubernetes-on-aws
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://172.17.0.87:6443
- name: test-cluster-1
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://172.17.0.87:6443
contexts:
- name: test-user@development
context:
cluster: development
user: test-user
- name: aws-user@kubernetes-on-aws
context:
cluster: kubernetes-on-aws
user: aws-user
- name: test-user@production
context:
cluster: production
user: test-user
- name: research
context:
cluster: test-cluster-1
user: dev-user
users:
- name: test-user
user:
client-certificate: /etc/kubernetes/pki/users/test-user/test-user.crt
client-key: /etc/kubernetes/pki/users/test-user/test-user.key
- name: dev-user
user:
client-certificate: /etc/kubernetes/pki/users/dev-user/developer-user.crt
client-key: /etc/kubernetes/pki/users/dev-user/dev-user.key
- name: aws-user
user:
client-certificate: /etc/kubernetes/pki/users/aws-user/aws-user.crt
client-key: /etc/kubernetes/pki/users/aws-user/aws-user.key
current-context: test-user@development
preferences: {}
demokubeconfig
curl https://my-kube-playground:6443/api/v1/pods --key admin.key --cert admin.crt --cacert ca.crt
kubectl get pods --server my-kube-playground:6443/api/v1/pods \
--client-key admin.key \
--client-certificate admin.crt \
--certificate-authority ca.crt
Kubeconfig file:
------------------------------>
Clusters --> cluster names(Development, Production, Google etc...)
Contexts --> defines which user account can access to which cluster... admin@Development... devuser@Google
Users --> users(admin, devuser,produser) to get access to k8s cluster
MacBook-Pro:6.Security bharathdasaraju$ kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority: /Users/bharathdasaraju/.minikube/ca.crt
extensions:
- extension:
last-update: Thu, 23 Sep 2021 07:52:38 +08
provider: minikube.sigs.k8s.io
version: v1.20.0
name: cluster_info
server: https://127.0.0.1:32769
name: minikube
contexts:
- context:
cluster: minikube
extensions:
- extension:
last-update: Thu, 23 Sep 2021 07:52:38 +08
provider: minikube.sigs.k8s.io
version: v1.20.0
name: context_info
namespace: default
user: minikube
name: minikube
current-context: minikube
kind: Config
preferences: {}
users:
- name: minikube
user:
client-certificate: /Users/bharathdasaraju/.minikube/profiles/minikube/client.crt
client-key: /Users/bharathdasaraju/.minikube/profiles/minikube/client.key
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:~ bharathdasaraju$ kubectl config view --kubeconfig=bkr-config
apiVersion: v1
clusters:
- cluster:
certificate-authority: /Users/bharathdasaraju/.minikube/ca.crt
extensions:
- extension:
last-update: Thu, 23 Sep 2021 07:52:38 +08
provider: minikube.sigs.k8s.io
version: v1.20.0
name: cluster_info
server: https://127.0.0.1:32769
name: minikube
contexts:
- context:
cluster: minikube
extensions:
- extension:
last-update: Thu, 23 Sep 2021 07:52:38 +08
provider: minikube.sigs.k8s.io
version: v1.20.0
name: context_info
namespace: default
user: minikube
name: minikube
current-context: minikube
kind: Config
preferences: {}
users:
- name: minikube
user:
client-certificate: /Users/bharathdasaraju/.minikube/profiles/minikube/client.crt
client-key: /Users/bharathdasaraju/.minikube/profiles/minikube/client.key
MacBook-Pro:~ bharathdasaraju$
MacBook-Pro:~ bharathdasaraju$ kubectl config current-context --kubeconfig=bkr-config
minikube
MacBook-Pro:~ bharathdasaraju$
MacBook-Pro:~ bharathdasaraju$ kubectl config use-context prod-user@production
MacBook-Pro:~ bharathdasaraju$
- cluster:
certificate-authority: /Users/bharathdasaraju/.minikube/ca.crt
we can also pass certificate-authority-data: the contents of cert in base64 format.
demokubeconfiglabs
root@controlplane:~# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://controlplane:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
root@controlplane:~#
----------------------------------------------------------------------------------------->
root@controlplane:~# kubectl config view --kubeconfig=my-kube-config
apiVersion: v1
clusters:
- cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
name: development
- cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
name: kubernetes-on-aws
- cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
name: production
- cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
name: test-cluster-1
contexts:
- context:
cluster: kubernetes-on-aws
user: aws-user
name: aws-user@kubernetes-on-aws
- context:
cluster: test-cluster-1
user: dev-user
name: research
- context:
cluster: development
user: test-user
name: test-user@development
- context:
cluster: production
user: test-user
name: test-user@production
current-context: test-user@development
kind: Config
preferences: {}
users:
- name: aws-user
user:
client-certificate: /etc/kubernetes/pki/users/aws-user/aws-user.crt
client-key: /etc/kubernetes/pki/users/aws-user/aws-user.key
- name: dev-user
user:
client-certificate: /etc/kubernetes/pki/users/dev-user/developer-user.crt
client-key: /etc/kubernetes/pki/users/dev-user/dev-user.key
- name: test-user
user:
client-certificate: /etc/kubernetes/pki/users/test-user/test-user.crt
client-key: /etc/kubernetes/pki/users/test-user/test-user.key
root@controlplane:~#
root@controlplane:~# kubectl config use-context research --kubeconfig=my-kube-config
Switched to context "research".
root@controlplane:~#
root@controlplane:~# kubectl config current-context --kubeconfig=my-kube-config
research
root@controlplane:~#
root@controlplane:/etc/kubernetes/pki/users/dev-user# kubectl config current-context
research
root@controlplane:/etc/kubernetes/pki/users/dev-user#
APIGroups
curl https://kube-master:6443/version
curl https://kube-master:6443/api/v1/pods
/api
/version
/healthz
/metrics
/apis
/logs
API groups --> CoreGroups, Named Groups
core group /api
------------------------>
/v1
pods
namesaces
nodes
bindings
PV
PVS
events
rc
secrets
services
configmaps
named group /apis
---------------------------->
/apps
/extensions
/networking.k8s.io
/storage.k8s.io
/authentication.k8s.io
/certificates.k8s.io
/apps
/v1
/deployments
/replicasets
/statefulsets
/deployments
actions
-------->
list
get
create
delete
update
watch
root@minikube:/# curl https://localhost:8443/version/ -k
{
"major": "1",
"minor": "20",
"gitVersion": "v1.20.2",
"gitCommit": "faecb196815e248d3ecfb03c680a4507229c2a56",
"gitTreeState": "clean",
"buildDate": "2021-01-13T13:20:00Z",
"goVersion": "go1.15.5",
"compiler": "gc",
"platform": "linux/amd64"
}root@minikube:/#
MacBook-Pro:6.Security bharathdasaraju$ kubectl proxy
Starting to serve on 127.0.0.1:8001
"/livez",
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$ curl -ks http://localhost:8001 | jq
{
"paths": [
"/.well-known/openid-configuration",
"/api",
"/api/v1",
"/apis",
"/apis/",
"/apis/admissionregistration.k8s.io",
"/apis/admissionregistration.k8s.io/v1",
"/apis/admissionregistration.k8s.io/v1beta1",
"/apis/apiextensions.k8s.io",
"/apis/apiextensions.k8s.io/v1",
"/apis/apiextensions.k8s.io/v1beta1",
"/apis/apiregistration.k8s.io",
"/apis/apiregistration.k8s.io/v1",
"/apis/apiregistration.k8s.io/v1beta1",
"/apis/apps",
"/apis/apps/v1",
"/apis/authentication.k8s.io",
"/apis/authentication.k8s.io/v1",
"/apis/authentication.k8s.io/v1beta1",
"/apis/authorization.k8s.io",
"/apis/authorization.k8s.io/v1",
"/apis/authorization.k8s.io/v1beta1",
"/apis/autoscaling",
"/apis/autoscaling/v1",
"/apis/autoscaling/v2beta1",
"/apis/autoscaling/v2beta2",
"/apis/batch",
"/apis/batch/v1",
"/apis/batch/v1beta1",
"/apis/certificates.k8s.io",
"/apis/certificates.k8s.io/v1",
"/apis/certificates.k8s.io/v1beta1",
"/apis/coordination.k8s.io",
"/apis/coordination.k8s.io/v1",
"/apis/coordination.k8s.io/v1beta1",
"/apis/discovery.k8s.io",
"/apis/discovery.k8s.io/v1beta1",
"/apis/events.k8s.io",
"/apis/events.k8s.io/v1",
"/apis/events.k8s.io/v1beta1",
"/apis/extensions",
"/apis/extensions/v1beta1",
"/apis/flowcontrol.apiserver.k8s.io",
"/apis/flowcontrol.apiserver.k8s.io/v1beta1",
"/apis/metrics.k8s.io",
"/apis/metrics.k8s.io/v1beta1",
"/apis/networking.k8s.io",
"/apis/networking.k8s.io/v1",
"/apis/networking.k8s.io/v1beta1",
"/apis/node.k8s.io",
"/apis/node.k8s.io/v1",
"/apis/node.k8s.io/v1beta1",
"/apis/policy",
"/apis/policy/v1beta1",
"/apis/rbac.authorization.k8s.io",
"/apis/rbac.authorization.k8s.io/v1",
"/apis/rbac.authorization.k8s.io/v1beta1",
"/apis/scheduling.k8s.io",
"/apis/scheduling.k8s.io/v1",
"/apis/scheduling.k8s.io/v1beta1",
"/apis/storage.k8s.io",
"/apis/storage.k8s.io/v1",
"/apis/storage.k8s.io/v1beta1",
"/healthz",
"/healthz/autoregister-completion",
"/healthz/etcd",
"/healthz/log",
"/healthz/ping",
"/healthz/poststarthook/aggregator-reload-proxy-client-cert",
"/healthz/poststarthook/apiservice-openapi-controller",
"/healthz/poststarthook/apiservice-registration-controller",
"/healthz/poststarthook/apiservice-status-available-controller",
"/healthz/poststarthook/bootstrap-controller",
"/healthz/poststarthook/crd-informer-synced",
"/healthz/poststarthook/generic-apiserver-start-informers",
"/healthz/poststarthook/kube-apiserver-autoregistration",
"/healthz/poststarthook/priority-and-fairness-config-consumer",
"/healthz/poststarthook/priority-and-fairness-config-producer",
"/healthz/poststarthook/priority-and-fairness-filter",
"/healthz/poststarthook/rbac/bootstrap-roles",
"/healthz/poststarthook/scheduling/bootstrap-system-priority-classes",
"/healthz/poststarthook/start-apiextensions-controllers",
"/healthz/poststarthook/start-apiextensions-informers",
"/healthz/poststarthook/start-cluster-authentication-info-controller",
"/healthz/poststarthook/start-kube-aggregator-informers",
"/healthz/poststarthook/start-kube-apiserver-admission-initializer",
"/livez",
"/livez/autoregister-completion",
"/livez/etcd",
"/livez/log",
"/livez/ping",
"/livez/poststarthook/aggregator-reload-proxy-client-cert",
"/livez/poststarthook/apiservice-openapi-controller",
"/livez/poststarthook/apiservice-registration-controller",
"/livez/poststarthook/apiservice-status-available-controller",
"/livez/poststarthook/bootstrap-controller",
"/livez/poststarthook/crd-informer-synced",
"/livez/poststarthook/generic-apiserver-start-informers",
"/livez/poststarthook/kube-apiserver-autoregistration",
"/livez/poststarthook/priority-and-fairness-config-consumer",
"/livez/poststarthook/priority-and-fairness-config-producer",
"/livez/poststarthook/priority-and-fairness-filter",
"/livez/poststarthook/rbac/bootstrap-roles",
"/livez/poststarthook/scheduling/bootstrap-system-priority-classes",
"/livez/poststarthook/start-apiextensions-controllers",
"/livez/poststarthook/start-apiextensions-informers",
"/livez/poststarthook/start-cluster-authentication-info-controller",
"/livez/poststarthook/start-kube-aggregator-informers",
"/livez/poststarthook/start-kube-apiserver-admission-initializer",
"/logs",
"/metrics",
"/openapi/v2",
"/openid/v1/jwks",
"/readyz",
"/readyz/autoregister-completion",
"/readyz/etcd",
"/readyz/informer-sync",
"/readyz/log",
"/readyz/ping",
"/readyz/poststarthook/aggregator-reload-proxy-client-cert",
"/readyz/poststarthook/apiservice-openapi-controller",
"/readyz/poststarthook/apiservice-registration-controller",
"/readyz/poststarthook/apiservice-status-available-controller",
"/readyz/poststarthook/bootstrap-controller",
"/readyz/poststarthook/crd-informer-synced",
"/readyz/poststarthook/generic-apiserver-start-informers",
"/readyz/poststarthook/kube-apiserver-autoregistration",
"/readyz/poststarthook/priority-and-fairness-config-consumer",
"/readyz/poststarthook/priority-and-fairness-config-producer",
"/readyz/poststarthook/priority-and-fairness-filter",
"/readyz/poststarthook/rbac/bootstrap-roles",
"/readyz/poststarthook/scheduling/bootstrap-system-priority-classes",
"/readyz/poststarthook/start-apiextensions-controllers",
"/readyz/poststarthook/start-apiextensions-informers",
"/readyz/poststarthook/start-cluster-authentication-info-controller",
"/readyz/poststarthook/start-kube-aggregator-informers",
"/readyz/poststarthook/start-kube-apiserver-admission-initializer",
"/readyz/shutdown",
"/version"
]
}
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$ curl -ks http://localhost:8001/apis/apps/v1 | jq
{
"kind": "APIResourceList",
"apiVersion": "v1",
"groupVersion": "apps/v1",
"resources": [
{
"name": "controllerrevisions",
"singularName": "",
"namespaced": true,
"kind": "ControllerRevision",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"storageVersionHash": "85nkx63pcBU="
},
{
"name": "daemonsets",
"singularName": "",
"namespaced": true,
"kind": "DaemonSet",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"ds"
],
"categories": [
"all"
],
"storageVersionHash": "dd7pWHUlMKQ="
},
{
"name": "daemonsets/status",
"singularName": "",
"namespaced": true,
"kind": "DaemonSet",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "deployments",
"singularName": "",
"namespaced": true,
"kind": "Deployment",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"deploy"
],
"categories": [
"all"
],
"storageVersionHash": "8aSe+NMegvE="
},
{
"name": "deployments/scale",
"singularName": "",
"namespaced": true,
"group": "autoscaling",
"version": "v1",
"kind": "Scale",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "deployments/status",
"singularName": "",
"namespaced": true,
"kind": "Deployment",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "replicasets",
"singularName": "",
"namespaced": true,
"kind": "ReplicaSet",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"rs"
],
"categories": [
"all"
],
"storageVersionHash": "P1RzHs8/mWQ="
},
{
"name": "replicasets/scale",
"singularName": "",
"namespaced": true,
"group": "autoscaling",
"version": "v1",
"kind": "Scale",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "replicasets/status",
"singularName": "",
"namespaced": true,
"kind": "ReplicaSet",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "statefulsets",
"singularName": "",
"namespaced": true,
"kind": "StatefulSet",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"sts"
],
"categories": [
"all"
],
"storageVersionHash": "H+vl74LkKdo="
},
{
"name": "statefulsets/scale",
"singularName": "",
"namespaced": true,
"group": "autoscaling",
"version": "v1",
"kind": "Scale",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "statefulsets/status",
"singularName": "",
"namespaced": true,
"kind": "StatefulSet",
"verbs": [
"get",
"patch",
"update"
]
}
]
}
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$ curl -ks http://localhost:8001/api/v1 | jq
{
"kind": "APIResourceList",
"groupVersion": "v1",
"resources": [
{
"name": "bindings",
"singularName": "",
"namespaced": true,
"kind": "Binding",
"verbs": [
"create"
]
},
{
"name": "componentstatuses",
"singularName": "",
"namespaced": false,
"kind": "ComponentStatus",
"verbs": [
"get",
"list"
],
"shortNames": [
"cs"
]
},
{
"name": "configmaps",
"singularName": "",
"namespaced": true,
"kind": "ConfigMap",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"cm"
],
"storageVersionHash": "qFsyl6wFWjQ="
},
{
"name": "endpoints",
"singularName": "",
"namespaced": true,
"kind": "Endpoints",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"ep"
],
"storageVersionHash": "fWeeMqaN/OA="
},
{
"name": "events",
"singularName": "",
"namespaced": true,
"kind": "Event",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"ev"
],
"storageVersionHash": "r2yiGXH7wu8="
},
{
"name": "limitranges",
"singularName": "",
"namespaced": true,
"kind": "LimitRange",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"limits"
],
"storageVersionHash": "EBKMFVe6cwo="
},
{
"name": "namespaces",
"singularName": "",
"namespaced": false,
"kind": "Namespace",
"verbs": [
"create",
"delete",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"ns"
],
"storageVersionHash": "Q3oi5N2YM8M="
},
{
"name": "namespaces/finalize",
"singularName": "",
"namespaced": false,
"kind": "Namespace",
"verbs": [
"update"
]
},
{
"name": "namespaces/status",
"singularName": "",
"namespaced": false,
"kind": "Namespace",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "nodes",
"singularName": "",
"namespaced": false,
"kind": "Node",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"no"
],
"storageVersionHash": "XwShjMxG9Fs="
},
{
"name": "nodes/proxy",
"singularName": "",
"namespaced": false,
"kind": "NodeProxyOptions",
"verbs": [
"create",
"delete",
"get",
"patch",
"update"
]
},
{
"name": "nodes/status",
"singularName": "",
"namespaced": false,
"kind": "Node",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "persistentvolumeclaims",
"singularName": "",
"namespaced": true,
"kind": "PersistentVolumeClaim",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"pvc"
],
"storageVersionHash": "QWTyNDq0dC4="
},
{
"name": "persistentvolumeclaims/status",
"singularName": "",
"namespaced": true,
"kind": "PersistentVolumeClaim",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "persistentvolumes",
"singularName": "",
"namespaced": false,
"kind": "PersistentVolume",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"pv"
],
"storageVersionHash": "HN/zwEC+JgM="
},
{
"name": "persistentvolumes/status",
"singularName": "",
"namespaced": false,
"kind": "PersistentVolume",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "pods",
"singularName": "",
"namespaced": true,
"kind": "Pod",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"po"
],
"categories": [
"all"
],
"storageVersionHash": "xPOwRZ+Yhw8="
},
{
"name": "pods/attach",
"singularName": "",
"namespaced": true,
"kind": "PodAttachOptions",
"verbs": [
"create",
"get"
]
},
{
"name": "pods/binding",
"singularName": "",
"namespaced": true,
"kind": "Binding",
"verbs": [
"create"
]
},
{
"name": "pods/eviction",
"singularName": "",
"namespaced": true,
"group": "policy",
"version": "v1beta1",
"kind": "Eviction",
"verbs": [
"create"
]
},
{
"name": "pods/exec",
"singularName": "",
"namespaced": true,
"kind": "PodExecOptions",
"verbs": [
"create",
"get"
]
},
{
"name": "pods/log",
"singularName": "",
"namespaced": true,
"kind": "Pod",
"verbs": [
"get"
]
},
{
"name": "pods/portforward",
"singularName": "",
"namespaced": true,
"kind": "PodPortForwardOptions",
"verbs": [
"create",
"get"
]
},
{
"name": "pods/proxy",
"singularName": "",
"namespaced": true,
"kind": "PodProxyOptions",
"verbs": [
"create",
"delete",
"get",
"patch",
"update"
]
},
{
"name": "pods/status",
"singularName": "",
"namespaced": true,
"kind": "Pod",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "podtemplates",
"singularName": "",
"namespaced": true,
"kind": "PodTemplate",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"storageVersionHash": "LIXB2x4IFpk="
},
{
"name": "replicationcontrollers",
"singularName": "",
"namespaced": true,
"kind": "ReplicationController",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"rc"
],
"categories": [
"all"
],
"storageVersionHash": "Jond2If31h0="
},
{
"name": "replicationcontrollers/scale",
"singularName": "",
"namespaced": true,
"group": "autoscaling",
"version": "v1",
"kind": "Scale",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "replicationcontrollers/status",
"singularName": "",
"namespaced": true,
"kind": "ReplicationController",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "resourcequotas",
"singularName": "",
"namespaced": true,
"kind": "ResourceQuota",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"quota"
],
"storageVersionHash": "8uhSgffRX6w="
},
{
"name": "resourcequotas/status",
"singularName": "",
"namespaced": true,
"kind": "ResourceQuota",
"verbs": [
"get",
"patch",
"update"
]
},
{
"name": "secrets",
"singularName": "",
"namespaced": true,
"kind": "Secret",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"storageVersionHash": "S6u1pOWzb84="
},
{
"name": "serviceaccounts",
"singularName": "",
"namespaced": true,
"kind": "ServiceAccount",
"verbs": [
"create",
"delete",
"deletecollection",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"sa"
],
"storageVersionHash": "pbx9ZvyFpBE="
},
{
"name": "serviceaccounts/token",
"singularName": "",
"namespaced": true,
"group": "authentication.k8s.io",
"version": "v1",
"kind": "TokenRequest",
"verbs": [
"create"
]
},
{
"name": "services",
"singularName": "",
"namespaced": true,
"kind": "Service",
"verbs": [
"create",
"delete",
"get",
"list",
"patch",
"update",
"watch"
],
"shortNames": [
"svc"
],
"categories": [
"all"
],
"storageVersionHash": "0/CO1lhkEBI="
},
{
"name": "services/proxy",
"singularName": "",
"namespaced": true,
"kind": "ServiceProxyOptions",
"verbs": [
"create",
"delete",
"get",
"patch",
"update"
]
},
{
"name": "services/status",
"singularName": "",
"namespaced": true,
"kind": "Service",
"verbs": [
"get",
"patch",
"update"
]
}
]
}
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$
k8sAuthorization
once someone get into cluster...what they can do..... thats what authorization defines
What the devlopers can do in k8s cluster
what the external services can do in k8s cluster
we should be giving exact required roles and role binding to the deveopers and service accounts.
Different types of authorization mechanisms available:
---------------------------------------------------------------------------------------------->
1. Node authorization
--------------------->
--> NodeAuthorizer this used by kubelet to communicate with kube-apiserver
2. Attribute Based Access Controls(ABAC)
--------------------------------------->
we need to maintain a json file by having user(or) group based resource Access
if any update needed everytime we need to manually edit this policy json file.
{"kind": "Policy", "spec": { "user": "dev-user-1", "namespace": "*", "resource": "pods", "apiGroup": "*"}}
{"kind": "Policy", "spec": { "user": "dev-users", "namespace": "*", "resource": "pods", "apiGroup": "*"}}
3.RBAC
----------->
here we create a role and assign set of users/groups to that role
4.Webhook:
----------->
What if, if you want to outsource all the authorization mechanisms.
say you want to manage authorization externally not through the builtin mechanisms.
For example: "Open Policy Agent" is a third party tool which helps with admission control and authorization.
we can have a kubernetes makes an API call to the "open policy agent" with the information about the user and his access requirements.
And have the "open policy agent" decide if the user should be permitted or not.
5.AlwaysAllow
--------------------->
6.AlwaysDeny
------------------------------>
in the kube-apiserver service file we can specify which authorization mode is needed. Bydefault it is "AlwaysAllow" mode
--authorization-mode=Node,RBAC,Webhook
k8srole
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: developer
rules:
- apiGroups: [""] # for core API group its empty for the named API group need to specify the name
resources: ["pods"]
verbs:
- get
- list
- watch
- create
- update
- delete
- apiGroups: [""]
resources: ["ConfigMaP"]
verbs: ["create", "delete"]
k8srolebinding
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: devuser-developer-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: developer
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: dev-user
k8srolegranular
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: developer_granualr
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
resourceNames:
- "blue"
- "orange"
k8sRBAC
RoleBasedAccesControl(RBAC)
-------------------------------->
How to Create a role
==============================================>
MacBook-Pro:6.Security bharathdasaraju$ kubectl create role developer --verb=get --verb=list --verb=watch --resource=pods --dry-run=client -o yaml > deveoper-role.yaml
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl apply -f deveoper-role.yaml
role.rbac.authorization.k8s.io/developer created
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe role developer
Name: developer
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
pods [] [] [get list watch create update delete]
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl apply -f deveoper-role.yaml
role.rbac.authorization.k8s.io/developer configured
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe role developer
Name: developer
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
ConfigMaP [] [] [create delete]
pods [] [] [get list watch create update delete]
MacBook-Pro:6.Security bharathdasaraju$
Create a RoleBinding:
==============================================>
RoleBinding is to assign that created to role to specific user/group
MacBook-Pro:6.Security bharathdasaraju$ kubectl create rolebinding devuser-developer-binding --role=developer --user=dev-user --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: devuser-developer-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: developer
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: dev-user
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl create rolebinding devuser-developer-binding --role=developer --user=dev-user --dry-run=client -o yaml > devuser-developer-binding.yaml
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl apply -f devuser-developer-binding.yaml
rolebinding.rbac.authorization.k8s.io/devuser-developer-binding created
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe rolebinding devuser-developer-binding
Name: devuser-developer-binding
Labels: <none>
Annotations: <none>
Role:
Kind: Role
Name: developer
Subjects:
Kind Name Namespace
---- ---- ---------
User dev-user
MacBook-Pro:6.Security bharathdasaraju$
note that roles and rolebindings falls under the scope of the namespaces.
where as
clusterrole and clusterrolebinding falls under the scope of the cluster.
MacBook-Pro:6.Security bharathdasaraju$ kubectl get roles
NAME CREATED AT
developer 2021-09-23T07:32:54Z
MacBook-Pro:6.Security bharathdasaraju$ kubectl get rolebindings
NAME ROLE AGE
devuser-developer-binding Role/developer 4m25s
MacBook-Pro:6.Security bharathdasaraju$
how to check can i have acces to particular resource in kubernetes:
--------------------------------------------------------------------------------->
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i create deployments
yes
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i delete nodes
Warning: resource 'nodes' is not namespace scoped
yes
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i delete nodes --as dev-user
Warning: resource 'nodes' is not namespace scoped
no
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i delete secrets --as dev-user
no
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i create secrets --as dev-user
no
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i create services --as dev-user
no
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i create pods --as dev-user
yes
MacBook-Pro:6.Security bharathdasaraju$ kubectl auth can-i create configmaps --as dev-user
no
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl create role developer_granualr --verb=get --verb=list --verb=watch --resource=pods --dry-run=client -o yaml > deveoper_granualr-role.yaml
MacBook-Pro:6.Security bharathdasaraju$
we can also use "ResourceNames" to give access to certain pods alone.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: developer_granualr
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch"]
resourceNames: ["blue", "orange"]
k8sRBAClabs
root@controlplane:/etc/kubernetes/manifests# kubectl get roles
No resources found in default namespace.
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl get roles --all-namespaces
NAMESPACE NAME CREATED AT
blue developer 2021-09-23T08:54:07Z
kube-public kubeadm:bootstrap-signer-clusterinfo 2021-09-23T08:51:21Z
kube-public system:controller:bootstrap-signer 2021-09-23T08:51:19Z
kube-system extension-apiserver-authentication-reader 2021-09-23T08:51:19Z
kube-system kube-proxy 2021-09-23T08:51:24Z
kube-system kubeadm:kubelet-config-1.20 2021-09-23T08:51:20Z
kube-system kubeadm:nodes-kubeadm-config 2021-09-23T08:51:20Z
kube-system system::leader-locking-kube-controller-manager 2021-09-23T08:51:19Z
kube-system system::leader-locking-kube-scheduler 2021-09-23T08:51:19Z
kube-system system:controller:bootstrap-signer 2021-09-23T08:51:19Z
kube-system system:controller:cloud-provider 2021-09-23T08:51:19Z
kube-system system:controller:token-cleaner 2021-09-23T08:51:19Z
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl describe role kube-proxy -n kube-system
Name: kube-proxy
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
configmaps [] [kube-proxy] [get]
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl describe rolebindings kube-proxy -n kube-system
Name: kube-proxy
Labels: <none>
Annotations: <none>
Role:
Kind: Role
Name: kube-proxy
Subjects:
Kind Name Namespace
---- ---- ---------
Group system:bootstrappers:kubeadm:default-node-token
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl auth can-i list pods --as dev-user
no
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl get pods --as dev-user
Error from server (Forbidden): pods is forbidden: User "dev-user" cannot list resource "pods" in API group "" in the namespace "default"
root@controlplane:/etc/kubernetes/manifests#
Create the necessary roles and role bindings required for the dev-user to create, list and delete pods in the default namespace
Role: developer
Role Resources: pods
Role Actions: list
Role Actions: create
RoleBinding: dev-user-binding
RoleBinding: Bound to dev-user
root@controlplane:/etc/kubernetes/manifests# kubectl create role devloper --verb=create --verb=list --verb=delete --resource=pods --dry-run=client -o yaml > dev_role.yaml
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl create rolebinding dev-user-binding --role=developer --user=dev-user --dry-run=client -o yaml > dev_rolebinding.yaml
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl apply -f dev_rolebinding.yaml
rolebinding.rbac.authorization.k8s.io/dev-user-binding created
root@controlplane:/etc/kubernetes/manifests# kubectl get pods --as dev-user
NAME READY STATUS RESTARTS AGE
red-c898cbdc6-54wnb 1/1 Running 0 14m
red-c898cbdc6-gb459 1/1 Running 0 14m
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:/etc/kubernetes/manifests# kubectl get role
NAME CREATED AT
developer 2021-09-23T09:06:28Z
root@controlplane:/etc/kubernetes/manifests# kubectl get rolebinding
NAME ROLE AGE
dev-user-binding Role/developer 86s
root@controlplane:/etc/kubernetes/manifests#
root@controlplane:~# kubectl auth can-i list pods -n blue
yes
root@controlplane:~#
root@controlplane:~# kubectl create role deploy-role --verb=create --resource=deployments --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: blue
name: deploy-role
rules:
- apiGroups:
- apps
resources:
- deployments
verbs:
- create
root@controlplane:~#
root@controlplane:~# kubectl create rolebinding dev-user-deploy-binding --role=deploy-role --user=dev-user --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
namespace: blue
name: dev-user-deploy-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: deploy-role
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: dev-user
root@controlplane:~#
root@controlplane:~# kubectl apply -f deploy-role-rolebinding.yaml
role.rbac.authorization.k8s.io/deploy-role created
rolebinding.rbac.authorization.k8s.io/dev-user-deploy-binding created
root@controlplane:~# cat deploy-role-rolebinding.yaml
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: blue
name: deploy-role
rules:
- apiGroups:
- apps
- extensions
resources:
- deployments
verbs:
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
namespace: blue
name: dev-user-deploy-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: deploy-role
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: dev-user
root@controlplane:~#
role_rolebinding
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: blue
name: deploy-role
rules:
- apiGroups:
- apps
- extensions
resources:
- deployments
verbs:
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
namespace: blue
name: dev-user-deploy-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: deploy-role
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: dev-user
clusterrole
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cluster-admin
rules:
- apiGroups: [""]
resources: ["nodes"]
verbs: ["list", "get", "create", "delete"]
clusterrolebinding
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: cluster-admin-role-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: admin-user1
clusterrolebinding2
Cluster_Scoped_Resources:
-------------------------------------->
1. nodes
2. PV
3. clusterroles
4. clusterrolebindings
5. certificatesigningrequests
6. namespaces
namespaced resources:
-------------------------------------------------------------------------------------->
MacBook-Pro:6.Security bharathdasaraju$ kubectl api-resources --namespaced=true | sort
NAME SHORTNAMES APIGROUP NAMESPACED KIND
bindings true Binding
configmaps cm true ConfigMap
controllerrevisions apps true ControllerRevision
cronjobs cj batch true CronJob
daemonsets ds apps true DaemonSet
deployments deploy apps true Deployment
endpoints ep true Endpoints
endpointslices discovery.k8s.io true EndpointSlice
events ev true Event
events ev events.k8s.io true Event
horizontalpodautoscalers hpa autoscaling true HorizontalPodAutoscaler
ingresses ing extensions true Ingress
ingresses ing networking.k8s.io true Ingress
jobs batch true Job
leases coordination.k8s.io true Lease
limitranges limits true LimitRange
localsubjectaccessreviews authorization.k8s.io true LocalSubjectAccessReview
networkpolicies netpol networking.k8s.io true NetworkPolicy
persistentvolumeclaims pvc true PersistentVolumeClaim
poddisruptionbudgets pdb policy true PodDisruptionBudget
pods metrics.k8s.io true PodMetrics
pods po true Pod
podtemplates true PodTemplate
replicasets rs apps true ReplicaSet
replicationcontrollers rc true ReplicationController
resourcequotas quota true ResourceQuota
rolebindings rbac.authorization.k8s.io true RoleBinding
roles rbac.authorization.k8s.io true Role
secrets true Secret
serviceaccounts sa true ServiceAccount
services svc true Service
statefulsets sts apps true StatefulSet
MacBook-Pro:6.Security bharathdasaraju$
cluster scoped resources:
-------------------------------------------------------------------------------------->
MacBook-Pro:6.Security bharathdasaraju$ kubectl api-resources --namespaced=false | sort
NAME SHORTNAMES APIGROUP NAMESPACED KIND
apiservices apiregistration.k8s.io false APIService
certificatesigningrequests csr certificates.k8s.io false CertificateSigningRequest
clusterrolebindings rbac.authorization.k8s.io false ClusterRoleBinding
clusterroles rbac.authorization.k8s.io false ClusterRole
componentstatuses cs false ComponentStatus
csidrivers storage.k8s.io false CSIDriver
csinodes storage.k8s.io false CSINode
customresourcedefinitions crd,crds apiextensions.k8s.io false CustomResourceDefinition
flowschemas flowcontrol.apiserver.k8s.io false FlowSchema
ingressclasses networking.k8s.io false IngressClass
mutatingwebhookconfigurations admissionregistration.k8s.io false MutatingWebhookConfiguration
namespaces ns false Namespace
nodes metrics.k8s.io false NodeMetrics
nodes no false Node
persistentvolumes pv false PersistentVolume
podsecuritypolicies psp policy false PodSecurityPolicy
priorityclasses pc scheduling.k8s.io false PriorityClass
prioritylevelconfigurations flowcontrol.apiserver.k8s.io false PriorityLevelConfiguration
runtimeclasses node.k8s.io false RuntimeClass
selfsubjectaccessreviews authorization.k8s.io false SelfSubjectAccessReview
selfsubjectrulesreviews authorization.k8s.io false SelfSubjectRulesReview
storageclasses sc storage.k8s.io false StorageClass
subjectaccessreviews authorization.k8s.io false SubjectAccessReview
tokenreviews authentication.k8s.io false TokenReview
validatingwebhookconfigurations admissionregistration.k8s.io false ValidatingWebhookConfiguration
volumeattachments storage.k8s.io false VolumeAttachment
MacBook-Pro:6.Security bharathdasaraju$
how to authorize cluster wide resources in k8s
------------------------------------------------->
We can use 1. clusterroles
2. clusterrolebindings
MacBook-Pro:6.Security bharathdasaraju$ kubectl create clusterrole cluster-admin --verb=list --verb=get --verb=create --resource=nodes --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
creationTimestamp: null
name: cluster-admin
rules:
- apiGroups:
- ""
resources:
- nodes
verbs:
- list
- get
- create
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl apply -f clusterrole-clusterAdmin.yaml
Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply
clusterrole.rbac.authorization.k8s.io/cluster-admin configured
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl get clusterrole cluster-admin
NAME CREATED AT
cluster-admin 2021-09-04T06:52:21Z
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl create clusterrolebinding cluster-admin-role-binding --clusterrole=cluster-admin --user=admin-user1 --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: null
name: cluster-admin-role-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: admin-user1
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl create clusterrolebinding cluster-admin-role-binding --clusterrole=cluster-admin --user=admin-user1 --dry-run=client -o yaml > clusteradmin-clusterrolebinding.yaml
MacBook-Pro:6.Security bharathdasaraju$ kubectl apply -f clusteradmin-clusterrolebinding.yaml
clusterrolebinding.rbac.authorization.k8s.io/cluster-admin-role-binding created
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe clusterrolebinding cluster-admin-role-binding
Name: cluster-admin-role-binding
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: cluster-admin
Subjects:
Kind Name Namespace
---- ---- ---------
User admin-user1
MacBook-Pro:6.Security bharathdasaraju$
userclusterrolebinding
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: storage-admin
rules:
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "watch", "list", "create", "delete"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "watch", "list", "create", "delete"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: michelle-storage-admin
subjects:
- kind: User
name: michelle
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: storage-admin
apiGroup: rbac.authorization.k8s.io
clusterrolebindinglabs
root@controlplane:~# kubectl get clusterrole
NAME CREATED AT
admin 2021-09-23T10:29:16Z
cluster-admin 2021-09-23T10:29:15Z
edit 2021-09-23T10:29:16Z
flannel 2021-09-23T10:29:28Z
kubeadm:get-nodes 2021-09-23T10:29:19Z
system:aggregate-to-admin 2021-09-23T10:29:16Z
system:aggregate-to-edit 2021-09-23T10:29:16Z
system:aggregate-to-view 2021-09-23T10:29:16Z
system:auth-delegator 2021-09-23T10:29:16Z
system:basic-user 2021-09-23T10:29:15Z
system:certificates.k8s.io:certificatesigningrequests:nodeclient 2021-09-23T10:29:16Z
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 2021-09-23T10:29:16Z
system:certificates.k8s.io:kube-apiserver-client-approver 2021-09-23T10:29:16Z
system:certificates.k8s.io:kube-apiserver-client-kubelet-approver 2021-09-23T10:29:16Z
system:certificates.k8s.io:kubelet-serving-approver 2021-09-23T10:29:16Z
system:certificates.k8s.io:legacy-unknown-approver 2021-09-23T10:29:16Z
system:controller:attachdetach-controller 2021-09-23T10:29:16Z
system:controller:certificate-controller 2021-09-23T10:29:17Z
system:controller:clusterrole-aggregation-controller 2021-09-23T10:29:16Z
system:controller:cronjob-controller 2021-09-23T10:29:16Z
system:controller:daemon-set-controller 2021-09-23T10:29:16Z
system:controller:deployment-controller 2021-09-23T10:29:16Z
system:controller:disruption-controller 2021-09-23T10:29:16Z
system:controller:endpoint-controller 2021-09-23T10:29:16Z
system:controller:endpointslice-controller 2021-09-23T10:29:16Z
system:controller:endpointslicemirroring-controller 2021-09-23T10:29:16Z
system:controller:expand-controller 2021-09-23T10:29:16Z
system:controller:generic-garbage-collector 2021-09-23T10:29:16Z
system:controller:horizontal-pod-autoscaler 2021-09-23T10:29:16Z
system:controller:job-controller 2021-09-23T10:29:16Z
system:controller:namespace-controller 2021-09-23T10:29:16Z
system:controller:node-controller 2021-09-23T10:29:17Z
system:controller:persistent-volume-binder 2021-09-23T10:29:17Z
system:controller:pod-garbage-collector 2021-09-23T10:29:17Z
system:controller:pv-protection-controller 2021-09-23T10:29:17Z
system:controller:pvc-protection-controller 2021-09-23T10:29:17Z
system:controller:replicaset-controller 2021-09-23T10:29:17Z
system:controller:replication-controller 2021-09-23T10:29:17Z
system:controller:resourcequota-controller 2021-09-23T10:29:17Z
system:controller:root-ca-cert-publisher 2021-09-23T10:29:17Z
system:controller:route-controller 2021-09-23T10:29:17Z
system:controller:service-account-controller 2021-09-23T10:29:17Z
system:controller:service-controller 2021-09-23T10:29:17Z
system:controller:statefulset-controller 2021-09-23T10:29:17Z
system:controller:ttl-controller 2021-09-23T10:29:17Z
system:coredns 2021-09-23T10:29:20Z
system:discovery 2021-09-23T10:29:15Z
system:heapster 2021-09-23T10:29:16Z
system:kube-aggregator 2021-09-23T10:29:16Z
system:kube-controller-manager 2021-09-23T10:29:16Z
system:kube-dns 2021-09-23T10:29:16Z
system:kube-scheduler 2021-09-23T10:29:16Z
system:kubelet-api-admin 2021-09-23T10:29:16Z
system:monitoring 2021-09-23T10:29:15Z
system:node 2021-09-23T10:29:16Z
system:node-bootstrapper 2021-09-23T10:29:16Z
system:node-problem-detector 2021-09-23T10:29:16Z
system:node-proxier 2021-09-23T10:29:16Z
system:persistent-volume-provisioner 2021-09-23T10:29:16Z
system:public-info-viewer 2021-09-23T10:29:15Z
system:service-account-issuer-discovery 2021-09-23T10:29:16Z
system:volume-scheduler 2021-09-23T10:29:16Z
view 2021-09-23T10:29:16Z
root@controlplane:~# kubectl get clusterrole | wc -l
64
root@controlplane:~#
root@controlplane:~# kubectl get clusterrolebindings
NAME ROLE AGE
cluster-admin ClusterRole/cluster-admin 4m9s
flannel ClusterRole/flannel 3m58s
kubeadm:get-nodes ClusterRole/kubeadm:get-nodes 4m7s
kubeadm:kubelet-bootstrap ClusterRole/system:node-bootstrapper 4m7s
kubeadm:node-autoapprove-bootstrap ClusterRole/system:certificates.k8s.io:certificatesigningrequests:nodeclient 4m7s
kubeadm:node-autoapprove-certificate-rotation ClusterRole/system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 4m7s
kubeadm:node-proxier ClusterRole/system:node-proxier 4m5s
system:basic-user ClusterRole/system:basic-user 4m9s
system:controller:attachdetach-controller ClusterRole/system:controller:attachdetach-controller 4m9s
system:controller:certificate-controller ClusterRole/system:controller:certificate-controller 4m8s
system:controller:clusterrole-aggregation-controller ClusterRole/system:controller:clusterrole-aggregation-controller 4m9s
system:controller:cronjob-controller ClusterRole/system:controller:cronjob-controller 4m9s
system:controller:daemon-set-controller ClusterRole/system:controller:daemon-set-controller 4m9s
system:controller:deployment-controller ClusterRole/system:controller:deployment-controller 4m9s
system:controller:disruption-controller ClusterRole/system:controller:disruption-controller 4m9s
system:controller:endpoint-controller ClusterRole/system:controller:endpoint-controller 4m9s
system:controller:endpointslice-controller ClusterRole/system:controller:endpointslice-controller 4m9s
system:controller:endpointslicemirroring-controller ClusterRole/system:controller:endpointslicemirroring-controller 4m9s
system:controller:expand-controller ClusterRole/system:controller:expand-controller 4m9s
system:controller:generic-garbage-collector ClusterRole/system:controller:generic-garbage-collector 4m9s
system:controller:horizontal-pod-autoscaler ClusterRole/system:controller:horizontal-pod-autoscaler 4m9s
system:controller:job-controller ClusterRole/system:controller:job-controller 4m9s
system:controller:namespace-controller ClusterRole/system:controller:namespace-controller 4m9s
system:controller:node-controller ClusterRole/system:controller:node-controller 4m9s
system:controller:persistent-volume-binder ClusterRole/system:controller:persistent-volume-binder 4m9s
system:controller:pod-garbage-collector ClusterRole/system:controller:pod-garbage-collector 4m8s
system:controller:pv-protection-controller ClusterRole/system:controller:pv-protection-controller 4m8s
system:controller:pvc-protection-controller ClusterRole/system:controller:pvc-protection-controller 4m8s
system:controller:replicaset-controller ClusterRole/system:controller:replicaset-controller 4m8s
system:controller:replication-controller ClusterRole/system:controller:replication-controller 4m8s
system:controller:resourcequota-controller ClusterRole/system:controller:resourcequota-controller 4m8s
system:controller:root-ca-cert-publisher ClusterRole/system:controller:root-ca-cert-publisher 4m8s
system:controller:route-controller ClusterRole/system:controller:route-controller 4m8s
system:controller:service-account-controller ClusterRole/system:controller:service-account-controller 4m8s
system:controller:service-controller ClusterRole/system:controller:service-controller 4m8s
system:controller:statefulset-controller ClusterRole/system:controller:statefulset-controller 4m8s
system:controller:ttl-controller ClusterRole/system:controller:ttl-controller 4m8s
system:coredns ClusterRole/system:coredns 4m6s
system:discovery ClusterRole/system:discovery 4m9s
system:kube-controller-manager ClusterRole/system:kube-controller-manager 4m9s
system:kube-dns ClusterRole/system:kube-dns 4m9s
system:kube-scheduler ClusterRole/system:kube-scheduler 4m9s
system:monitoring ClusterRole/system:monitoring 4m9s
system:node ClusterRole/system:node 4m9s
system:node-proxier ClusterRole/system:node-proxier 4m9s
system:public-info-viewer ClusterRole/system:public-info-viewer 4m9s
system:service-account-issuer-discovery ClusterRole/system:service-account-issuer-discovery 4m9s
system:volume-scheduler ClusterRole/system:volume-scheduler 4m9s
root@controlplane:~# kubectl get clusterrolebindings | wc -l
49
root@controlplane:~#
root@controlplane:~# kubectl create clusterrole michelle-cluster-role --verb=create,list,delete --resource=nodes --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: michelle-cluster-role
rules:
- apiGroups:
- ""
resources:
- nodes
verbs:
- create
- list
- delete
root@controlplane:~#
root@controlplane:~# kubectl create clusterrolebinding michelle-clusterbinding --clusterrole=michelle-cluster-admin --user=michelle --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: null
name: michelle-clusterbinding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: michelle-cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: michelle
root@controlplane:~# ls -rtlh
total 4.0K
-rw-rw-rw- 1 root root 0 Sep 14 01:32 sample.yaml
-rw-r--r-- 1 root root 201 Sep 23 10:40 michelle-cluster-roles.yaml
root@controlplane:~# vim michelle-cluster-roles.yaml
root@controlplane:~# kubectl apply -f michelle-cluster-roles.yaml
clusterrole.rbac.authorization.k8s.io/michelle-cluster-role created
clusterrolebinding.rbac.authorization.k8s.io/michelle-clusterbinding created
root@controlplane:~#
michelles responsibilities are growing and now she will be responsible for storage as well.
Create the required ClusterRoles and ClusterRoleBindings to allow her access to Storage.
Get the API groups and resource names from command kubectl api-resources.
ClusterRole: storage-admin
Resource: persistentvolumes
Resource: storageclasses
ClusterRoleBinding: michelle-storage-admin
ClusterRoleBinding Subject: michelle
ClusterRoleBinding Role: storage-admin
Get the API groups and resource names from command kubectl api-resources. Use the given spec:
root@controlplane:~# kubectl api-resources --namespaced=false | grep -i storage
csidrivers storage.k8s.io/v1 false CSIDriver
csinodes storage.k8s.io/v1 false CSINode
storageclasses sc storage.k8s.io/v1 false StorageClass
volumeattachments storage.k8s.io/v1 false VolumeAttachment
root@controlplane:~# kubectl api-resources --namespaced=false | grep -i volumes
persistentvolumes pv v1 false PersistentVolume
root@controlplane:~#
root@controlplane:~# cat michelle-cluster.yaml
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: storage-admin
rules:
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "watch", "list", "create", "delete"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "watch", "list", "create", "delete"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: michelle-storage-admin
subjects:
- kind: User
name: michelle
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: storage-admin
apiGroup: rbac.authorization.k8s.io
root@controlplane:~#
root@controlplane:~# vim michelle-cluster.yaml
root@controlplane:~# kubectl apply -f michelle-cluster.yaml
clusterrole.rbac.authorization.k8s.io/storage-admin created
clusterrolebinding.rbac.authorization.k8s.io/michelle-storage-admin created
root@controlplane:~#
k8sserviceaccount
service accounts in kubernetes:
------------------------------------>
There are two types of accounts in k8s
1. User accounts --> used by users
user accounts is an administrator who performing the cluster upgrade or node reboot :)
2. Service accounts --> used by machines
A service account could be an account used by an application to interact with a kubernetes cluster.
For example: A monitoring application like prometheus uses a service account to poll the kubernetes API for performance metrics
and an automated build tool like jenkins uses a service account to deploy the application in kubernetes cluster.
MacBook-Pro:6.Security bharathdasaraju$ kubectl create serviceaccount dashboard-sa
serviceaccount/dashboard-sa created
MacBook-Pro:6.Security bharathdasaraju$ kubectl get sa
NAME SECRETS AGE
dashboard-sa 1 42s
default 1 19d
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe sa dashboard-sa
Name: dashboard-sa
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: dashboard-sa-token-zvz8j
Tokens: dashboard-sa-token-zvz8j
Events: <none>
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe secret dashboard-sa-token-zvz8j
Name: dashboard-sa-token-zvz8j
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-sa
kubernetes.io/service-account.uid: f8f95fe6-d654-4cac-a8c2-26d50d4995df
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1066 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjNZMmtub0JrMENOVG91QW1TdUYwR1RKUTRkTEJldXdaUllCaDhKOGFlLVkifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRhc2hib2FyZC1zYS10b2tlbi16dno4aiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkYXNoYm9hcmQtc2EiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJmOGY5NWZlNi1kNjU0LTRjYWMtYThjMi0yNmQ1MGQ0OTk1ZGYiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkYXNoYm9hcmQtc2EifQ.m1SBFXAh1UBxyDbyo8q4C3b55oE_GKZv3YW6kwF_IuEz0s9oVYa4i0G7nh8zs1LB2D6mrwGK2G9Y9BV6dH08woCdXJJOpkZH_h8gdwAMWVsMByuBJUwwm-hyRx0X7-O332v6kjhCd7XDQ8TPfz2GLMKC2YO9m_Oe3E1EbQkBWfzJnFHoIN7mWwwvHXdeov3rlDQSxM7MwxHx4JHT1NoSu15SJarcOQ8LXsulYW394InejrR1eQBwYa9yLBuN0Fgj8QwWqY60hJihd-T9vGqfuzRGm3FWePhosZirVjiajR2-pwAAd2o5cfCpr5ZPO4WKdoMLs81r4KOLB4Wbh_RB_A
MacBook-Pro:6.Security bharathdasaraju$
We can use this token as "Bearer Token" to query the kubernetes API and get the resutls to our app.
curl https://192.168.56.70:6443/api --insecure --header "Authorization: Bearer eyJhbGciOiJSU....81r4KOLB4Wbh_RB_A"
if you run the application inside the same kubernetes cluster, we can mount the secret token as a volume so that it automatically availble inside a pod.
MacBook-Pro:6.Security bharathdasaraju$ kubectl get sa
NAME SECRETS AGE
dashboard-sa 1 9m21s
default 1 19d
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe sa default
Name: default
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: default-token-lxpp9
Tokens: default-token-lxpp9
Events: <none>
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe secret default-token-lxpp9
Name: default-token-lxpp9
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: default
kubernetes.io/service-account.uid: 7a0dc882-5dd6-4233-90c7-e8502644250e
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjNZMmtub0JrMENOVG91QW1TdUYwR1RKUTRkTEJldXdaUllCaDhKOGFlLVkifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtdG9rZW4tbHhwcDkiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjdhMGRjODgyLTVkZDYtNDIzMy05MGM3LWU4NTAyNjQ0MjUwZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.DNsKGkklsdZ9dpaTH_hT29tHhD3-HiFQ8lctdPGaZGudKSkfe2nSEFoWsc5nO_sqrAg-t-s4ZLf5xsR1cYfbdh7Dqshx5MFS9RzZN5gy05em7Q3aoKfx3nXtN8wsnHlWejSAgrTUYjIhcmy3lJCFWZzFQO66OScVI2Dl9tqXM8plnLEmHGSd-InEZSI4B_Y4EWlYQi6Q8rQBzHVnn1pioztQzIQlhDIw0s0D7MGikVLdWChNDn0fdHqcBbGGasS0jxHrtu9WbYGy26q3ZqIjEsgGzygOv15L92AAnmXYcvDMcMKlRcRgpH02kodWLrmMxSj9-3pnXfkwqcoRqRBfOA
ca.crt: 1066 bytes
namespace: 7 bytes
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl run nginx --image=nginx
pod/nginx created
MacBook-Pro:6.Security bharathdasaraju$
"if we deacribe the pod....we can see below secret token mounted to pod"
"========================================================================================================="
Containers:
nginx:
Container ID: docker://f4fcdfa20357c5fcd21548a564214ecc6c9eb7bb0a08c4f385ec8cb65791c02d
Image: nginx
Image ID: docker-pullable://nginx@sha256:853b221d3341add7aaadf5f81dd088ea943ab9c918766e295321294b035f3f3e
Port: <none>
Host Port: <none>
State: Running
Started: Thu, 23 Sep 2021 21:19:33 +0800
Ready: True
Restart Count: 0
Environment: <none>
Mounts:
/var/run/secrets/kubernetes.io/serviceaccount from default-token-lxpp9 (ro)
Volumes:
default-token-lxpp9:
Type: Secret (a volume populated by a Secret)
SecretName: default-token-lxpp9
Optional: false
"============================================================================================="
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe pod nginx
Name: nginx
Namespace: default
Priority: 0
Node: minikube/192.168.49.2
Start Time: Thu, 23 Sep 2021 21:19:26 +0800
Labels: run=nginx
Annotations: <none>
Status: Running
IP: 172.17.0.4
IPs:
IP: 172.17.0.4
Containers:
nginx:
Container ID: docker://f4fcdfa20357c5fcd21548a564214ecc6c9eb7bb0a08c4f385ec8cb65791c02d
Image: nginx
Image ID: docker-pullable://nginx@sha256:853b221d3341add7aaadf5f81dd088ea943ab9c918766e295321294b035f3f3e
Port: <none>
Host Port: <none>
State: Running
Started: Thu, 23 Sep 2021 21:19:33 +0800
Ready: True
Restart Count: 0
Environment: <none>
Mounts:
/var/run/secrets/kubernetes.io/serviceaccount from default-token-lxpp9 (ro)
Conditions:
Type Status
Initialized True
Ready True
ContainersReady True
PodScheduled True
Volumes:
default-token-lxpp9:
Type: Secret (a volume populated by a Secret)
SecretName: default-token-lxpp9
Optional: false
QoS Class: BestEffort
Node-Selectors: <none>
Tolerations: node.kubernetes.io/not-ready:NoExecute op=Exists for 300s
node.kubernetes.io/unreachable:NoExecute op=Exists for 300s
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Scheduled 16s default-scheduler Successfully assigned default/nginx to minikube
Normal Pulling 15s kubelet Pulling image "nginx"
Normal Pulled 9s kubelet Successfully pulled image "nginx" in 5.7508824s
Normal Created 9s kubelet Created container nginx
Normal Started 9s kubelet Started container nginx
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl run nginx --image=nginx --dry-run=client -o yaml > pod_with_serviceaccount.yaml
MacBook-Pro:6.Security bharathdasaraju$
By default ....default serviceaccount token gets mounted to pod specification file.
if you do not want default service account to get mounted to pod we need use "automountServiceAccountToken: false"
apiVersion: v1
kind: Pod
metadata:
labels:
run: nginx
name: nginx
spec:
containers:
- image: nginx
name: nginx
automountServiceAccountToken: false
k8sserviceaccountlabs
root@controlplane:/# kubectl get sa
NAME SECRETS AGE
default 1 13m
root@controlplane:/#
root@controlplane:/# kubectl describe sa default
Name: default
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: default-token-xvpxp
Tokens: default-token-xvpxp
Events: <none>
root@controlplane:/#
The application needs a ServiceAccount with the Right permissions to be created to authenticate to Kubernetes.
The 'default' ServiceAccount has limited access. Create a new ServiceAccount named 'dashboard-sa'.
root@controlplane:/var/rbac# kubectl get sa
NAME SECRETS AGE
dashboard-sa 1 42s
default 1 23m
root@controlplane:/var/rbac# kubectl describe sa dashboard-sa
Name: dashboard-sa
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: dashboard-sa-token-b7qmk
Tokens: dashboard-sa-token-b7qmk
Events: <none>
root@controlplane:/var/rbac#
root@controlplane:/var/rbac# pwd
/var/rbac
root@controlplane:/var/rbac# ls -lrth
total 8.0K
-rw-rw-rw- 1 root root 191 Sep 14 01:32 pod-reader-role.yaml
-rw-rw-rw- 1 root root 399 Sep 14 01:32 dashboard-sa-role-binding.yaml
root@controlplane:/var/rbac#
root@controlplane:/var/rbac# cat pod-reader-role.yaml
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups:
- ''
resources:
- pods
verbs:
- get
- watch
- list
root@controlplane:/var/rbac#
root@controlplane:/var/rbac# cat dashboard-sa-role-binding.yaml
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: ServiceAccount
name: dashboard-sa # Name is case sensitive
namespace: default
roleRef:
kind: Role #this must be Role or ClusterRole
name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to
apiGroup: rbac.authorization.k8s.io
root@controlplane:/var/rbac#
root@controlplane:/var/rbac# kubectl describe sa dashboard-sa
Name: dashboard-sa
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: dashboard-sa-token-b7qmk
Tokens: dashboard-sa-token-b7qmk
Events: <none>
root@controlplane:/var/rbac# kubectl describe secrets dashboard-sa-token-b7qmk
Name: dashboard-sa-token-b7qmk
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-sa
kubernetes.io/service-account.uid: 52508e72-5bcb-4c89-952b-d9c9b47c9d0d
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1066 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InlDaGMxZXhicXpIMUZrQUlJR3dfTm5DTVBBaDUzYUtwTzZLWmZRdjBjUjAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRhc2hib2FyZC1zYS10b2tlbi1iN3FtayIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkYXNoYm9hcmQtc2EiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI1MjUwOGU3Mi01YmNiLTRjODktOTUyYi1kOWM5YjQ3YzlkMGQiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkYXNoYm9hcmQtc2EifQ.GcDrsRVcSZ2O4obe-q5MkK04-AVAzZNHysk_F-gr5_eXaXcxDU2bVTD3Rulahf6bmPg5HVZ-XigVs3JbAzTSCd2dngz3I55yaQ1lqTxq6wwvVb7hidnUkI2i7sFZQNVRUW_54BuArhFDIRjGpbiTn0J8rpzbHdww3sb6YEZWyhvHRIbAO5VXTxGIfLFRCjwOUBe_g2Gd6r8ChXFT5WOac4MHJUCPRBIhIn0fgH1b2vpBzYXy_BaN_Gy1Q5702LGbyBzfiKNWph9D8Mxkgd_ynISZi79vK8UjsIK5XSduE-XpPma6GDBly0ZK9OLJI2iAAXoMxdoISSzqjjPU5ZhGew
root@controlplane:/var/rbac#
root@controlplane:~# kubectl edit deployment.apps/web-dashboard
deployment.apps/web-dashboard edited
root@controlplane:~#
spec:
serviceAccountName: dashboard-sa
containers:
- image: gcr.io/kodekloud/customimage/my-kubernetes-dashboard
imagePullPolicy: Always
name: web-dashboard
ports:
- containerPort: 8080
protocol: TCP
deploymentwithSA
apiVersion: apps/v1
kind: Deployment
metadata:
name: web-dashboard
namespace: default
spec:
replicas: 1
selector:
matchLabels:
name: web-dashboard
strategy:
rollingUpdate:
maxSurge: 25%
maxUnavailable: 25%
type: RollingUpdate
template:
metadata:
creationTimestamp: null
labels:
name: web-dashboard
spec:
serviceAccountName: dashboard-sa
containers:
- image: gcr.io/kodekloud/customimage/my-kubernetes-dashboard
imagePullPolicy: Always
name: web-dashboard
ports:
- containerPort: 8080
protocol: TCP
k8sdashboardrole
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups:
- ''
resources:
- pods
verbs:
- get
- watch
- list
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: ServiceAccount
name: dashboard-sa # Name is case sensitive
namespace: default
roleRef:
kind: Role #this must be Role or ClusterRole
name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to
apiGroup: rbac.authorization.k8s.io
secureImages
MacBook-Pro:6.Security bharathdasaraju$ kubectl create deployment webapp --image=nginx
deployment.apps/webapp created
MacBook-Pro:6.Security bharathdasaraju$
the deployment to use a new image from myprivateregistry.com:5000
The registry is located at myprivateregistry.com:5000
Create a secret object with the credentials required to access the registry.
Name: private-reg-cred
Username: dock_user
Password: dock_password
Server: myprivateregistry.com:5000
Email: dock_user@myprivateregistry.com
Secret: private-reg-cred
Secret Type: docker-registry
Secret Data
MacBook-Pro:6.Security bharathdasaraju$ kubectl create secret docker-registry private-reg-cred --docker-server=myprivateregistry.com:5000 --docker-username=dock_user --docker-password=dock_password --docker-email=test@gmail.com
secret/private-reg-cred created
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe secret private-reg-cred
Name: private-reg-cred
Namespace: default
Labels: <none>
Annotations: <none>
Type: kubernetes.io/dockerconfigjson
Data
====
.dockerconfigjson: 159 bytes
MacBook-Pro:6.Security bharathdasaraju$
kubectl edit deploy web command and add "imagePullSecrets" section. Use private-reg-cred
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: webapp
name: webapp
spec:
replicas: 1
selector:
matchLabels:
app: webapp
strategy:
rollingUpdate:
maxSurge: 25%
maxUnavailable: 25%
type: RollingUpdate
template:
metadata:
labels:
app: webapp
spec:
containers:
- image: myprivateregistry.com:5000/nginx:alpine
name: nginx
imagePullSecrets:
- name: private-reg-cred
podwithSA
apiVersion: v1
kind: Pod
metadata:
labels:
run: nginx
name: nginx
spec:
containers:
- image: nginx
name: nginx
serviceAccountName: dashboard-sa
dockercredsinpod
apiVersion: v1
kind: Pod
metadata:
labels:
run: nginx
name: nginx
spec:
containers:
- image: private-registry.io/apps/internal-app
name: nginx
imagePullSecrets:
- name: regcred
deploymentwithdockercreds
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: webapp
name: webapp
spec:
replicas: 1
selector:
matchLabels:
app: webapp
strategy:
rollingUpdate:
maxSurge: 25%
maxUnavailable: 25%
type: RollingUpdate
template:
metadata:
labels:
app: webapp
spec:
containers:
- image: myprivateregistry.com:5000/nginx:alpine
name: nginx
imagePullSecrets:
- name: private-reg-cred
imagesecurity
--image=nginx --> pulled from dokerhub i.e. docker.io/nginx/nginx
gcr.io/kubernetes-e2e-test-image/dnsutils
docker login private-registry.io
docker run private-registry.io/apps/internal-app
how to pass docker login credentials for kubernetes, we can use k8s secret object to pass credentials of private registry.
MacBook-Pro:6.Security bharathdasaraju$ kubectl create secret docker-registry regcred \
> --docker-server=private-registry.io/apps/internal-app \
> --docker-username=bharath \
> --docker-password=password12345 \
> --docker-email=bhrth.dsra1@gmail.com
secret/regcred created
MacBook-Pro:6.Security bharathdasaraju$ kubectl describe secret regcred
Name: regcred
Namespace: default
Labels: <none>
Annotations: <none>
Type: kubernetes.io/dockerconfigjson
Data
====
.dockerconfigjson: 171 bytes
MacBook-Pro:6.Security bharathdasaraju$
MacBook-Pro:6.Security bharathdasaraju$ kubectl run nginx --image=private-registry.io/apps/internal-app --dry-run=client -o yaml
apiVersion: v1
kind: Pod
metadata:
labels:
run: nginx
name: nginx
spec:
containers:
- image: private-registry.io/apps/internal-app
name: nginx
imagePullSecrets:
- name: regcred
MacBook-Pro:6.Security bharathdasaraju$
dockersecurity
MacBook-Pro:6.Security bharathdasaraju$ docker run ubuntu sleep 100
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$ docker ps | grep -i ubuntu
909d1fe5ebab ubuntu "sleep 100" 40 seconds ago Up 39 seconds inspiring_dijkstra
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$
Inside docker container:
---------------------------->
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$ docker exec -it a0d647aee08e sh
# ps
PID TTY TIME CMD
6 pts/0 00:00:00 sh
11 pts/0 00:00:00 ps
# ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.1 0.0 2508 516 ? Ss 23:55 0:00 sleep 100
root 6 0.5 0.0 2608 604 pts/0 Ss 23:56 0:00 sh
root 12 0.0 0.1 5896 2776 pts/0 R+ 23:56 0:00 ps aux
#
In the host:
------------------------------------------------------------------------------------------------------------------------------->
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$ ps aux | grep -i sleep
bharathdasaraju 13768 0.0 0.0 4268408 688 s003 R+ 7:13am 0:00.00 grep -i sleep
bharathdasaraju 13711 0.0 0.1 4436660 21436 s002 S+ 7:12am 0:00.06 /usr/local/bin/com.docker.cli run ubuntu sleep 100
bharathdasaraju 13708 0.0 0.1 5038428 15224 s002 S+ 7:12am 0:00.04 docker run ubuntu sleep 100
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$
by default docker runs processes with-in the container as a root user.
if we dont want to run the processees as root user with-in the contaier we can set the "--user=user_id" while running the docker run
MacBook-Pro:6.Security bharathdasaraju$ docker run --user=1000 ubuntu sleep 100
MacBook-Pro:certified_kubernetes_administrator bharathdasaraju$ docker exec -it a0a3ea054709 sh
$ ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
1000 1 0.0 0.0 2508 580 ? Ss 00:01 0:00 sleep 100
1000 6 0.3 0.0 2608 596 pts/0 Ss 00:02 0:00 sh
1000 12 0.0 0.1 5896 2836 pts/0 R+ 00:02 0:00 ps aux
$
We can also set this in Dockerfile:
Dockerfile:
----------------->
FROM ubuntu
USER 1000
Linux Capabilities:
------------------------->
/usr/include/linux/capability.sh
docker run --cap-add MAC_ADMIN ubuntu
docker run --cap-drop KILL ubuntu
docker run --privileged ubuntu
securitycontexts
in kubernetes containers are encapsulated in pods.
We can choose to configure security settings at a container level and a pod level.
MacBook-Pro:6.Security bharathdasaraju$ kubectl run webpod --image=ubuntu --command -- "sleep 100" --dry-run=client -o yaml
pod/webpod created
MacBook-Pro:6.Security bharathdasaraju$ kubectl run webpod --image=ubuntu --dry-run=client -o yaml --command -- "sleep 100"
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
run: webpod
name: webpod
spec:
containers:
- command:
- sleep 100
image: ubuntu
name: webpod
resources: {}
dnsPolicy: ClusterFirst
restartPolicy: Always
status: {}
MacBook-Pro:6.Security bharathdasaraju$
securityContext configured at pod level:
------------------------------------------------------------------>
apiVersion: v1
kind: Pod
metadata:
labels:
run: webpod
name: webpod
spec:
securityContext:
runAsUser: 1000
containers:
- command: ["sleep", "100"]
image: ubuntu
name: webpod
securityContext configured at container level:
------------------------------------------------------------------>
apiVersion: v1
kind: Pod
metadata:
labels:
run: webpod
name: webpod
spec:
containers:
- command: ["sleep", "100"]
image: ubuntu
name: webpod
securityContext:
runAsUser: 1000
capabilities:
add: ["MAC_ADMIN"]
podsecuritycontext
apiVersion: v1
kind: Pod
metadata:
labels:
run: webpod
name: webpod
spec:
securityContext:
runAsUser: 1000
containers:
- command: ["sleep", "100"]
image: ubuntu
name: webpod
containersecuritycontext
apiVersion: v1
kind: Pod
metadata:
labels:
run: webpod
name: webpod
spec:
containers:
- command: ["sleep", "100"]
image: ubuntu
name: webpod
securityContext:
runAsUser: 1000
capabilities:
add: ["MAC_ADMIN"]
multipodsecuritycontext
apiVersion: v1
kind: Pod
metadata:
name: multi-pod
spec:
securityContext:
runAsUser: 1001
containers:
- image: ubuntu
name: web
command: ["sleep", "5000"]
securityContext:
runAsUser: 1002
- image: ubuntu
name: sidecar
command: ["sleep", "5000"]
securitycontextslabs
root@controlplane:~# kubectl get pods
NAME READY STATUS RESTARTS AGE
ubuntu-sleeper 1/1 Running 0 22s
root@controlplane:~# kubectl get pods ubuntu-sleeper -o yaml
apiVersion: v1
kind: Pod
metadata:
name: ubuntu-sleeper
namespace: default
spec:
containers:
- command:
- sleep
- "4800"
image: ubuntu
imagePullPolicy: Always
name: ubuntu
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
volumeMounts:
- mountPath: /var/run/secrets/kubernetes.io/serviceaccount
name: default-token-pkzgr
readOnly: true
dnsPolicy: ClusterFirst
enableServiceLinks: true
nodeName: controlplane
preemptionPolicy: PreemptLowerPriority
priority: 0
restartPolicy: Always
schedulerName: default-scheduler
securityContext:
runAsUser: 1010
serviceAccount: default
serviceAccountName: default
terminationGracePeriodSeconds: 30
tolerations:
- effect: NoExecute
key: node.kubernetes.io/not-ready
operator: Exists
tolerationSeconds: 300
- effect: NoExecute
key: node.kubernetes.io/unreachable
operator: Exists
tolerationSeconds: 300
volumes:
- name: default-token-pkzgr
secret:
defaultMode: 420
secretName: default-token-pkzgr
root@controlplane:~#
root@controlplane:~# kubectl delete pod ubuntu-sleeper
pod "ubuntu-sleeper" deleted
kubectl appltroot@controlplane:~#
root@controlplane:~# kubectl apply -f /tmp/kubectl-edit-vquy1.yaml
pod/ubuntu-sleeper created
root@controlplane:~# kubectl exec -it ubuntu-sleeper sh
kubectl exec [POD] [COMMAND] is DEPRECATED and will be removed in a future version. Use kubectl exec [POD] -- [COMMAND] instead.
$ id
uid=1010 gid=0(root) groups=0(root)
$
root@controlplane:~# cat multi-pod.yaml
apiVersion: v1
kind: Pod
metadata:
name: multi-pod
spec:
securityContext:
runAsUser: 1001
containers:
- image: ubuntu
name: web
command: ["sleep", "5000"]
securityContext:
runAsUser: 1002
- image: ubuntu
name: sidecar
command: ["sleep", "5000"]
root@controlplane:~#
Update pod ubuntu-sleeper to run as Root user and with the SYS_TIME capability.
----------------------------------------------------------------------------------------->
apiVersion: v1
kind: Pod
metadata:
name: ubuntu-sleeper
namespace: default
spec:
containers:
- command:
- sleep
- "4800"
image: ubuntu
imagePullPolicy: Always
name: ubuntu
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
volumeMounts:
- mountPath: /var/run/secrets/kubernetes.io/serviceaccount
name: default-token-pkzgr
readOnly: true
dnsPolicy: ClusterFirst
enableServiceLinks: true
nodeName: controlplane
preemptionPolicy: PreemptLowerPriority
priority: 0
restartPolicy: Always
schedulerName: default-scheduler
securityContext:
capabilities:
add: ["SYS_TIME"]
serviceAccount: default
serviceAccountName: default
terminationGracePeriodSeconds: 30
tolerations:
- effect: NoExecute
key: node.kubernetes.io/not-ready
operator: Exists
tolerationSeconds: 300
- effect: NoExecute
key: node.kubernetes.io/unreachable
operator: Exists
tolerationSeconds: 300
volumes:
- name: default-token-pkzgr
secret:
defaultMode: 420
secretName: default-token-pkzgr
--------------------------pod.yaml------------------------->
apiVersion: v1
kind: Pod
metadata:
name: ubuntu-sleeper
namespace: default
spec:
containers:
- command:
- sleep
- "4800"
image: ubuntu
name: ubuntu-sleeper
securityContext:
capabilities:
add: ["SYS_TIME", "NET_ADMIN"]
--------------------------------------------------------------------->
root@controlplane:~# vim pod.yaml
root@controlplane:~#
root@controlplane:~# kubectl apply -f pod.yaml
pod/ubuntu-sleeper created
root@controlplane:~#
networkpolicies
network security:
Ingress and Egress rules for ... webpods <--> appication pods <--> Database pods
Web-Pod <----> API-Pod <----> DB-Pod
by default all pods can communicate with eachother in k8s cluster.
and we want to restrict Web-Pods only be able to talk to API-Pods and only API-Pods be able to talk to DB-Pods.
for this we need to implement network policy.
NetworkPolicy is another kubernetes object.
how to attach network policy to pods...hmmm we use labels and selectors :)
Solutions that support network policies are:
1.Kube-router
2.Calico
3.Weave-net
4.Romana
developnetworkpolicy
apiversion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: db-policy
spec:
podSelector:
matchLabels:
role: db
policyTypes:
- Ingress
- Egress
ingress:
- from:
- podSelector:
matchLabels:
name: api-pod
namespaceSelector:
matchLabels:
name: prod
- ipBlock:
cidr: 192.168.5.10/32 # Lets say another backup server needs to connect to the API pod for the databackup purpose
ports:
- protocol: TCP
port: 3306
egress:
- to:
- ipBlock:
cidr: 192.168.5.10/32 #an agent from Db-pod trying to push data to the external backup server
ports:
- protocol: TCP
port: 80
networkpolicylabs
root@controlplane:~# kubectl get netpol
NAME POD-SELECTOR AGE
payroll-policy name=payroll 4m28s
root@controlplane:~#
root@controlplane:~# kubectl describe netpol payroll-policy
Name: payroll-policy
Namespace: default
Created on: 2021-09-24 04:51:36 +0000 UTC
Labels: <none>
Annotations: <none>
Spec:
PodSelector: name=payroll
Allowing ingress traffic:
To Port: 8080/TCP
From:
PodSelector: name=internal
Not affecting egress traffic
Policy Types: Ingress
root@controlplane:~#
the policy means traffic from internal pod can access port 8080 on payroll pod is allowed.
root@controlplane:~# kubectl get pods
NAME READY STATUS RESTARTS AGE
external 1/1 Running 0 7m35s
internal 1/1 Running 0 7m35s
mysql 1/1 Running 0 7m35s
payroll 1/1 Running 0 7m35s
root@controlplane:~#
Create a network policy to allow traffic from the Internal application only to the payroll-service and db-service.
Use the spec given on the below. You might want to enable ingress traffic to the pod to test your rules in the UI.
Policy Name: internal-policy
Policy Type: Egress
Egress Allow: payroll
Payroll Port: 8080
Egress Allow: mysql
MySQL Port: 3306
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: internal-policy
namespace: default
spec:
podSelector:
matchLabels:
name: internal
policyTypes:
- Egress
- Ingress
ingress:
- {}
egress:
- to:
- podSelector:
matchLabels:
name: mysql
ports:
- protocol: TCP
port: 3306
- to:
- podSelector:
matchLabels:
name: payroll
ports:
- protocol: TCP
port: 8080
- ports:
- port: 53
protocol: UDP
- port: 53
protocol: TCP
Note: We have also allowed Egress traffic to TCP and UDP port.
This has been added to ensure that the internal DNS resolution works from the internal pod.
Remember: The kube-dns service is exposed on port 53:
root@controlplane:~# kubectl apply -f internal-policy-updated.yaml
networkpolicy.networking.k8s.io/internal-policy created
root@controlplane:~# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 66m
root@controlplane:~#
ingress_egress_networkpolicy
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: internal-policy
namespace: default
spec:
podSelector:
matchLabels:
name: internal
policyTypes:
- Egress
- Ingress
ingress:
- {}
egress:
- to:
- podSelector:
matchLabels:
name: mysql
ports:
- protocol: TCP
port: 3306
- to:
- podSelector:
matchLabels:
name: payroll
ports:
- protocol: TCP
port: 8080
- ports:
- port: 53
protocol: UDP
- port: 53
protocol: TCP
samplenetworkpolicy
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: db-policy
spec:
podSelector:
matchLabels:
role: db
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
name: api-pod
ports:
- protocol: TCP
port: 3306
CA Pulic certs in Browsers
CA public certs in chrome -
CA public certs in firefox -
all k8s TLS certs
all k8s TLS certs -
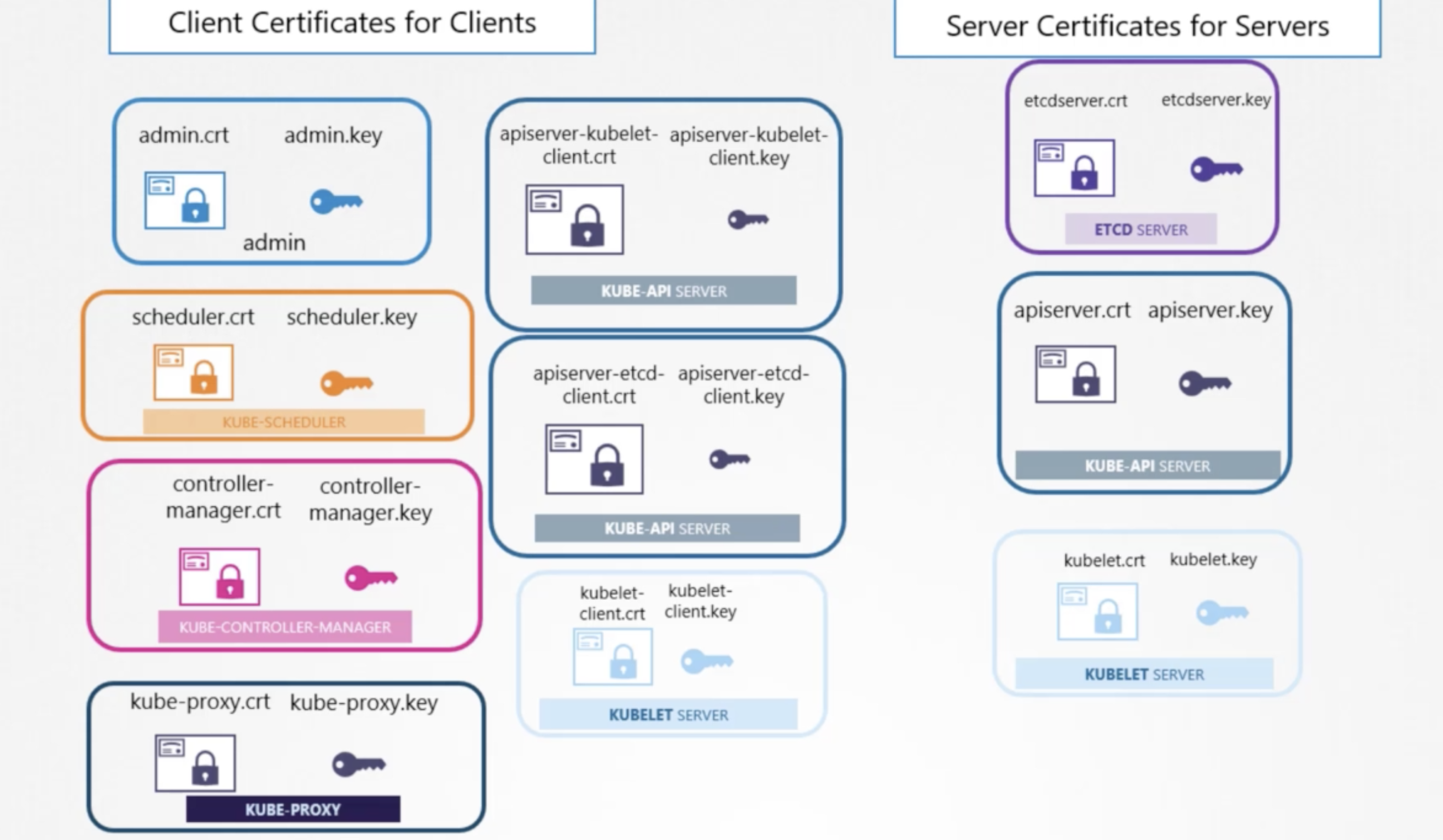
configure TLS public/private keys
TLS public/private keys at TLS.
configure TLS for k8s
TLS in kubernetes tlsink8s.